TLS vs HTTPS: Understanding the Key Differences for Secure Communication
In the realm of cybersecurity and online communication, understanding the protocols that safeguard our data is paramount. Two terms that frequently surface are TLS (Transport Layer Security) and HTTPS (Hypertext Transfer Protocol Secure). While often used interchangeably, they represent distinct yet interconnected components of secure web communication. This article delves into the nuances of TLS vs HTTPS, exploring their individual roles, their relationship, and why both are crucial for maintaining a secure online environment.
What is TLS?
Transport Layer Security, or TLS, is a cryptographic protocol designed to provide secure communication over a network. It’s the successor to Secure Sockets Layer (SSL), although the term SSL is still often used colloquially. TLS operates at the transport layer of the TCP/IP model, ensuring that data transmitted between two communicating applications is encrypted and authenticated. This means that any eavesdropper intercepting the data stream would only see gibberish, unable to decipher the sensitive information being exchanged.
TLS achieves this security through several key mechanisms:
- Encryption: TLS uses cryptographic algorithms to encrypt data, protecting it from unauthorized access.
- Authentication: TLS verifies the identity of the communicating parties, ensuring that you’re communicating with the intended server and not an imposter. This is typically done using digital certificates.
- Integrity: TLS ensures that the data transmitted hasn’t been tampered with during transit. This prevents malicious actors from altering the data without detection.
Think of TLS as the security guard ensuring the safe passage of a valuable package. It verifies the sender and recipient, encrypts the package contents, and ensures that the package arrives intact.
What is HTTPS?
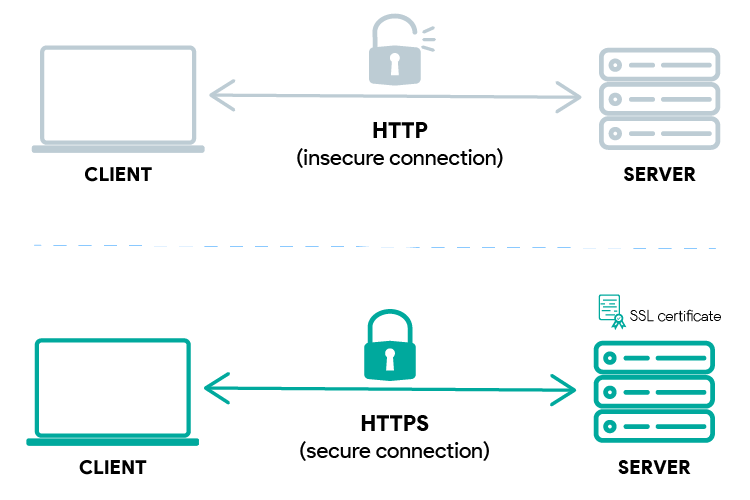
Hypertext Transfer Protocol Secure, or HTTPS, is the secure version of HTTP, the protocol used to transfer data over the web. HTTPS isn’t a protocol on its own; rather, it’s HTTP operating over a secure TLS (or SSL) connection. In essence, HTTPS is HTTP fortified with the security features provided by TLS.
When you see “https://” at the beginning of a website’s address, it indicates that the communication between your browser and the website’s server is encrypted using TLS. This encryption protects your data, such as login credentials, credit card information, and browsing history, from being intercepted by malicious actors.
HTTPS provides the following benefits:
- Confidentiality: HTTPS encrypts the data exchanged between the user’s browser and the web server, preventing eavesdropping.
- Integrity: HTTPS ensures that the data transmitted hasn’t been altered during transit, protecting against man-in-the-middle attacks.
- Authentication: While not inherent to HTTP itself, the TLS layer used by HTTPS allows for server authentication, verifying the identity of the website you’re connecting to.
- SEO Boost: Search engines like Google prioritize HTTPS websites, giving them a ranking boost in search results.
Therefore, HTTPS can be viewed as the armored car that transports the HTTP data. The armored car (TLS) provides the security, while the HTTP data is the valuable cargo being transported.
Key Differences Between TLS and HTTPS
The core difference between TLS vs HTTPS lies in their roles and layers within the network communication model. TLS is a protocol that provides secure communication by encrypting data, authenticating parties, and ensuring data integrity. It operates at the transport layer. HTTPS, on the other hand, is HTTP operating over a TLS (or SSL) connection. It’s the application of TLS to secure web traffic.
Here’s a table summarizing the key differences:
| Feature | TLS | HTTPS |
|---|---|---|
| Protocol Type | Cryptographic protocol | Application protocol (HTTP) secured by TLS |
| Layer in TCP/IP Model | Transport Layer | Application Layer |
| Function | Provides secure communication channel | Secures web traffic |
| Dependency | Independent protocol | Relies on TLS (or SSL) for security |
Why Both TLS and HTTPS are Important
Both TLS and HTTPS are essential for creating a secure online environment. TLS provides the underlying security mechanisms that enable secure communication, while HTTPS applies these mechanisms to secure web traffic. Without TLS, HTTPS wouldn’t exist. Without HTTPS, sensitive data transmitted over the web would be vulnerable to interception and manipulation. The combination of TLS and HTTPS ensures that our online interactions are protected, fostering trust and security in the digital world.
The importance of TLS and HTTPS extends beyond simply protecting sensitive data. They also play a crucial role in:
- Building Trust: Seeing the “https://” prefix and the padlock icon in the browser’s address bar assures users that their connection is secure, building trust and encouraging them to interact with the website.
- Improving SEO: Search engines like Google prioritize HTTPS websites, leading to better search engine rankings.
- Complying with Regulations: Many regulations, such as GDPR and HIPAA, require the use of HTTPS to protect sensitive data.
- Preventing Man-in-the-Middle Attacks: HTTPS helps prevent man-in-the-middle attacks, where an attacker intercepts communication between a user and a server and potentially steals or modifies data.
Implementing TLS and HTTPS
Implementing TLS and HTTPS involves obtaining a digital certificate from a Certificate Authority (CA) and configuring your web server to use the certificate. The CA verifies your identity and issues a certificate that confirms the authenticity of your website. Once the certificate is installed on your server, your server can use it to establish secure TLS connections with clients.
The process typically involves the following steps:
- Choose a Certificate Authority: Select a reputable CA to obtain your digital certificate.
- Generate a Certificate Signing Request (CSR): Create a CSR on your server, which contains information about your website and organization.
- Submit the CSR to the CA: Submit the CSR to the CA, along with the required documentation.
- Install the Certificate: Once the CA verifies your information, they will issue a digital certificate. Install the certificate on your web server.
- Configure your Web Server: Configure your web server to use the certificate for HTTPS connections.
- Test your Configuration: Test your HTTPS configuration to ensure that it is working correctly.
Numerous resources and tutorials are available online to guide you through this process, specific to your web server software (e.g., Apache, Nginx, IIS). [See also: Choosing the Right SSL Certificate]
The Future of Secure Communication
As technology continues to evolve, so too will the protocols and methods used to secure online communication. TLS is constantly being updated with new versions and security enhancements to address emerging threats. The migration to HTTPS is becoming increasingly prevalent, with most modern browsers actively discouraging or blocking non-HTTPS websites.
Furthermore, new technologies like HTTP/3, which uses QUIC (Quick UDP Internet Connections) as its transport protocol, are being developed to improve performance and security. QUIC incorporates TLS encryption by default, further solidifying the importance of secure communication in the future web.
Conclusion
In conclusion, understanding the difference between TLS vs HTTPS is crucial for anyone involved in web development, cybersecurity, or simply navigating the internet safely. TLS is the underlying protocol that provides secure communication, while HTTPS is the application of TLS to secure web traffic. Both are essential for protecting our data, building trust, and fostering a secure online environment. By implementing TLS and HTTPS, we can collectively contribute to a safer and more trustworthy digital world. Ignoring the importance of TLS and HTTPS leaves systems vulnerable to attack. Make sure your systems are configured to use HTTPS and the latest version of TLS for optimal security. [See also: Best Practices for TLS Configuration]
