Forward Proxy vs. Reverse Proxy: Understanding the Key Differences
In the realm of network architecture and cybersecurity, proxies play a crucial role in managing traffic, enhancing security, and improving performance. Among the various types of proxies, forward proxies and reverse proxies are two of the most commonly used. While both serve as intermediaries between clients and servers, they operate in fundamentally different ways. Understanding the distinctions between a forward proxy and a reverse proxy is essential for making informed decisions about network design and security implementation. This article will delve into the intricacies of each, highlighting their core functionalities, use cases, and advantages.
What is a Forward Proxy?
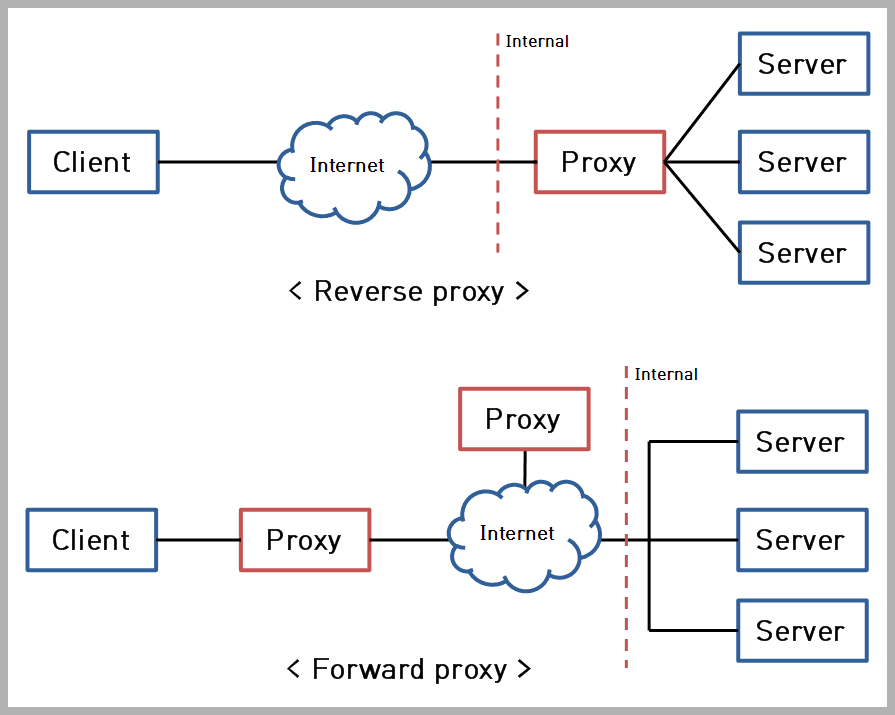
A forward proxy acts as an intermediary for requests originating from within a private network to external servers on the internet. Think of it as a gatekeeper for outgoing traffic. When a client inside the network makes a request to a website or service outside the network, the request is first routed to the forward proxy. The forward proxy then forwards the request to the destination server on behalf of the client. The response from the server is sent back to the forward proxy, which then relays it to the original client.
Key Characteristics of a Forward Proxy
- Client-Facing: A forward proxy primarily serves the needs of clients within a private network.
- Outbound Traffic Management: It manages and controls outbound traffic, ensuring that requests to external servers are properly handled.
- Anonymity: By masking the client’s IP address, a forward proxy provides a degree of anonymity. The destination server only sees the IP address of the proxy server, not the client’s actual IP.
- Caching: Forward proxies can cache frequently accessed content, reducing latency and bandwidth usage for clients.
- Content Filtering: They can be configured to filter content, blocking access to certain websites or types of content based on organizational policies.
Use Cases for Forward Proxies
Forward proxies are commonly used in various scenarios, including:
- Bypassing Geolocation Restrictions: Users in countries with internet censorship can use forward proxies to access content that is blocked in their region.
- Improving Network Performance: Caching capabilities of forward proxies reduce network congestion and improve response times.
- Enhancing Security: By acting as a single point of entry for outbound traffic, forward proxies can enforce security policies and prevent malicious traffic from leaving the network.
- Monitoring and Logging: Forward proxies provide a centralized point for monitoring and logging network activity, allowing administrators to track user behavior and identify potential security threats.
What is a Reverse Proxy?
A reverse proxy, on the other hand, acts as an intermediary for requests coming from external clients to one or more internal servers. It sits in front of the servers and intercepts incoming requests. Clients connect to the reverse proxy, which then forwards the requests to the appropriate backend server. The response from the server is sent back to the reverse proxy, which then relays it to the client.
Key Characteristics of a Reverse Proxy
- Server-Facing: A reverse proxy primarily serves the needs of servers within a private network.
- Inbound Traffic Management: It manages and controls inbound traffic, ensuring that requests to internal servers are properly handled.
- Load Balancing: Reverse proxies can distribute traffic across multiple backend servers, preventing any single server from being overloaded.
- Security: They can protect backend servers from direct exposure to the internet, mitigating the risk of attacks.
- SSL Encryption: Reverse proxies can handle SSL encryption and decryption, offloading this task from the backend servers.
- Caching: Similar to forward proxies, reverse proxies can also cache content to improve performance.
Use Cases for Reverse Proxies
Reverse proxies are essential components in many modern web architectures and are used in various scenarios, including:
- Load Balancing: Distributing traffic across multiple servers to ensure high availability and performance.
- Security: Protecting backend servers from direct access and mitigating DDoS attacks.
- SSL Termination: Handling SSL encryption and decryption to reduce the load on backend servers.
- Caching: Caching static content to improve response times and reduce bandwidth usage.
- Centralized Authentication: Implementing a single point of authentication for multiple applications.
Forward Proxy vs. Reverse Proxy: Key Differences Summarized
The fundamental difference between a forward proxy and a reverse proxy lies in their purpose and the direction of traffic they handle. A forward proxy protects clients by hiding their IP addresses and controlling outbound traffic, while a reverse proxy protects servers by hiding their IP addresses and managing inbound traffic. Here’s a summary of the key differences:
| Feature | Forward Proxy | Reverse Proxy |
|---|---|---|
| Purpose | Protects clients | Protects servers |
| Traffic Direction | Outbound | Inbound |
| Client Visibility | Clients are aware they are using a proxy | Clients are unaware they are using a proxy |
| Server Visibility | Servers only see the proxy’s IP | Clients only see the proxy’s IP |
| Common Use Cases | Bypassing restrictions, improving performance, enhancing security for clients | Load balancing, security, SSL termination, caching for servers |
Real-World Examples
To further illustrate the differences, consider these real-world examples:
- Forward Proxy Example: A company uses a forward proxy to allow its employees to access the internet while monitoring and controlling their web activity. The forward proxy also caches frequently accessed websites to improve network performance.
- Reverse Proxy Example: A popular e-commerce website uses a reverse proxy to distribute traffic across multiple servers. The reverse proxy also handles SSL encryption and decryption, and caches static content to improve website performance.
Benefits of Using Proxies
Both forward proxies and reverse proxies offer numerous benefits, including:
- Enhanced Security: Protecting clients and servers from direct exposure to the internet.
- Improved Performance: Caching content and load balancing traffic to reduce latency and improve response times.
- Increased Anonymity: Masking IP addresses to protect privacy.
- Centralized Management: Providing a single point for monitoring and controlling network traffic.
Choosing the Right Proxy
The choice between a forward proxy and a reverse proxy depends on the specific needs of your network and applications. If you need to protect clients and control outbound traffic, a forward proxy is the right choice. If you need to protect servers and manage inbound traffic, a reverse proxy is the better option. [See also: Proxy Server Benefits]. In some cases, you may even need to use both types of proxies to achieve the desired level of security and performance.
Conclusion
Understanding the differences between a forward proxy and a reverse proxy is crucial for designing secure and efficient network architectures. While both serve as intermediaries, they operate in distinct ways and address different needs. By carefully considering your specific requirements, you can choose the right type of proxy to enhance security, improve performance, and protect your valuable data. The forward proxy focuses on client-side protection, while the reverse proxy secures the server-side. Both are indispensable tools in modern network management. The implementation of either a forward proxy or a reverse proxy, or even both, depends heavily on the architecture and security requirements of the network. Choosing between a forward proxy and reverse proxy is thus a critical decision for network administrators. This comparison of forward proxy and reverse proxy should provide a solid foundation for making those decisions.
