HTTPS TLS: Securing Web Communication in the Modern Era
In today’s digital landscape, secure communication is paramount. One of the most fundamental technologies enabling this security on the web is HTTPS, which relies on Transport Layer Security (TLS). This article delves into the intricacies of HTTPS TLS, exploring its importance, how it works, and its evolution in ensuring secure online interactions. Understanding HTTPS TLS is crucial for anyone involved in web development, cybersecurity, or simply navigating the internet safely.
What is HTTPS?
HTTPS (Hypertext Transfer Protocol Secure) is the secure version of HTTP, the protocol over which data is sent between your browser and the website you are connected to. The ‘S’ at the end of HTTPS stands for ‘Secure’, meaning all communications between your browser and the website are encrypted. This encryption is provided by TLS.
The Role of TLS
TLS (Transport Layer Security) is a cryptographic protocol designed to provide communication security over a computer network. It is the successor to Secure Sockets Layer (SSL). TLS encrypts segments of network connections at the Transport Layer, providing end-to-end security of data transmitted between applications. Think of TLS as the protective shield around your data as it travels across the internet.
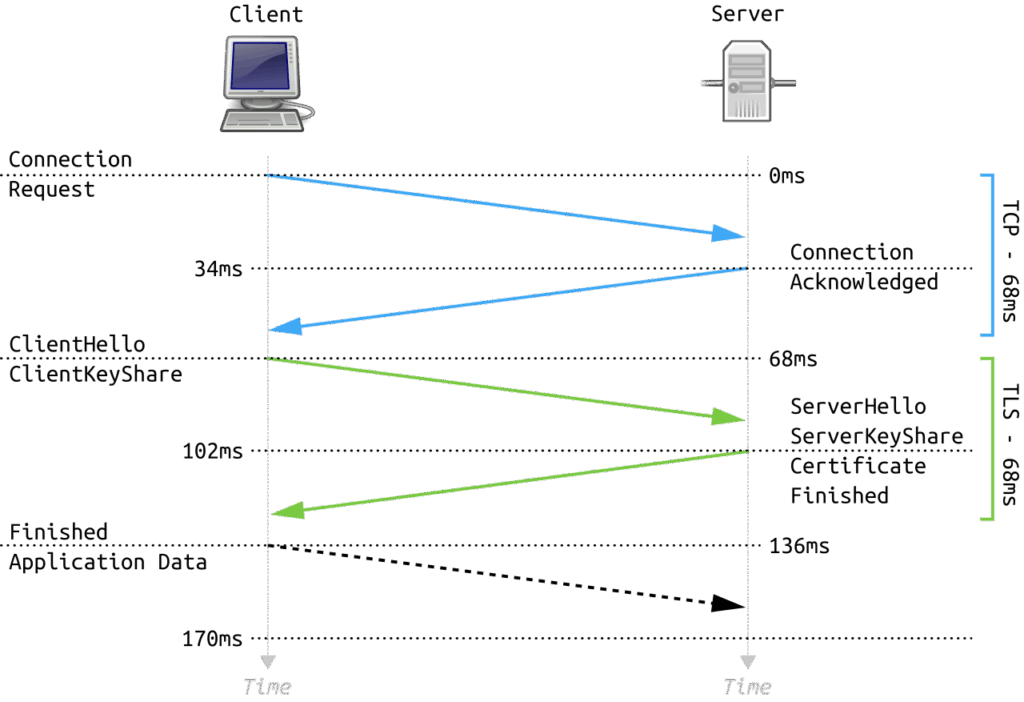
How TLS Works
The TLS handshake process is a crucial part of establishing a secure connection. It involves several steps:
- Client Hello: The client (your browser) sends a message to the server, specifying which TLS versions and cipher suites it supports.
- Server Hello: The server responds with its chosen TLS version and cipher suite. It also sends its digital certificate, which contains the server’s public key.
- Authentication: The client verifies the server’s certificate with a Certificate Authority (CA). This ensures that the server is who it claims to be.
- Key Exchange: The client generates a symmetric encryption key and encrypts it with the server’s public key. This encrypted key is sent to the server.
- Encryption: Both the client and server use the symmetric key to encrypt all subsequent data transmitted between them.
This complex process ensures that even if an attacker intercepts the communication, they cannot decrypt the data without the symmetric key.
Why is HTTPS TLS Important?
The importance of HTTPS TLS cannot be overstated. It provides several critical benefits:
- Encryption: Protects data from eavesdropping. This is particularly important for sensitive information like passwords, credit card numbers, and personal data.
- Authentication: Verifies the identity of the server. This prevents man-in-the-middle attacks, where an attacker intercepts communication and impersonates the server.
- Data Integrity: Ensures that data is not tampered with during transmission. This prevents attackers from modifying data in transit.
- SEO Benefits: Search engines like Google prioritize HTTPS websites in their search rankings. This means that having HTTPS TLS can improve your website’s visibility.
- User Trust: HTTPS provides a visual cue to users that the website is secure. This can increase user trust and confidence in the website.
The Evolution of TLS
TLS has undergone several revisions since its inception. Each version has addressed security vulnerabilities and improved performance. Some key milestones include:
- SSL 1.0, 2.0, and 3.0: The predecessors to TLS. SSL 1.0 was never released due to security flaws. SSL 2.0 and 3.0 were widely used but eventually found to have vulnerabilities.
- TLS 1.0: The first version of TLS, released in 1999. It addressed several security flaws in SSL 3.0.
- TLS 1.1: Released in 2006, it included improvements to cipher block chaining (CBC) protection and added support for padding oracle attacks.
- TLS 1.2: Released in 2008, it introduced stronger hash algorithms and improved cipher suite negotiation.
- TLS 1.3: The latest version of TLS, released in 2018. It significantly simplifies the handshake process, improves performance, and removes support for weaker and outdated cryptographic algorithms.
It is crucial to use the latest version of TLS to ensure the highest level of security. Older versions are vulnerable to known attacks and should be disabled.
Implementing HTTPS TLS
Implementing HTTPS TLS involves obtaining a TLS certificate from a Certificate Authority (CA) and configuring your web server to use the certificate. Here’s a general overview of the steps:
- Choose a Certificate Authority: Select a reputable CA. Popular options include Let’s Encrypt (free), DigiCert, and Comodo.
- Generate a Certificate Signing Request (CSR): Create a CSR on your web server. This CSR contains information about your domain and organization.
- Submit the CSR to the CA: Provide the CSR to the CA. They will verify your information and issue a TLS certificate.
- Install the Certificate: Install the TLS certificate on your web server. The specific steps will vary depending on your web server software (e.g., Apache, Nginx).
- Configure Your Web Server: Configure your web server to redirect all HTTP traffic to HTTPS. This ensures that all connections are secure.
There are numerous online resources and tutorials available to guide you through the implementation process for specific web server configurations.
Best Practices for HTTPS TLS Configuration
Even with HTTPS TLS implemented, it’s important to follow best practices to ensure optimal security:
- Use the Latest TLS Version: Always use the latest version of TLS (currently TLS 1.3) and disable older versions.
- Choose Strong Cipher Suites: Select strong cipher suites that use modern cryptographic algorithms. Avoid weak or outdated cipher suites.
- Enable HTTP Strict Transport Security (HSTS): HSTS instructs browsers to only connect to your website over HTTPS. This prevents man-in-the-middle attacks that attempt to downgrade connections to HTTP.
- Use Certificate Pinning: Certificate pinning allows you to specify which certificates are trusted for your website. This can prevent attackers from using fraudulently issued certificates.
- Regularly Update Your Software: Keep your web server software and TLS libraries up to date to patch security vulnerabilities.
- Monitor Your Certificate Expiry: Ensure that your TLS certificate is renewed before it expires. An expired certificate will cause browsers to display security warnings.
The Future of HTTPS TLS
The future of HTTPS TLS is likely to involve further improvements in performance, security, and automation. Some potential developments include:
- Quantum-Resistant Cryptography: As quantum computers become more powerful, they may be able to break current cryptographic algorithms. TLS will need to evolve to use quantum-resistant algorithms.
- Automated Certificate Management: Tools like Let’s Encrypt are making it easier to obtain and manage TLS certificates. This trend is likely to continue, with more automation and integration with cloud platforms.
- Improved Performance: Ongoing research is focused on improving the performance of TLS, reducing latency and improving the user experience.
Conclusion
HTTPS TLS is a cornerstone of secure web communication. By encrypting data, authenticating servers, and ensuring data integrity, it protects users from a wide range of online threats. Understanding how HTTPS TLS works and following best practices for its implementation are essential for anyone involved in web development or cybersecurity. As the internet continues to evolve, HTTPS TLS will remain a critical technology for ensuring a secure and trustworthy online experience. As cyber threats continue to evolve, staying informed about the latest advancements in HTTPS TLS and related security protocols is paramount. [See also: Understanding SSL Certificates] [See also: Best Practices for Website Security] [See also: The Importance of Data Encryption]
