How to Create a Web Proxy: A Comprehensive Guide
In today’s interconnected world, online privacy and security are paramount. A web proxy acts as an intermediary between your computer and the internet, providing an extra layer of protection and anonymity. Understanding how to create a web proxy can empower you to control your online experience and enhance your digital security. This comprehensive guide will walk you through the process, covering various methods and considerations for setting up your own web proxy.
Understanding Web Proxies
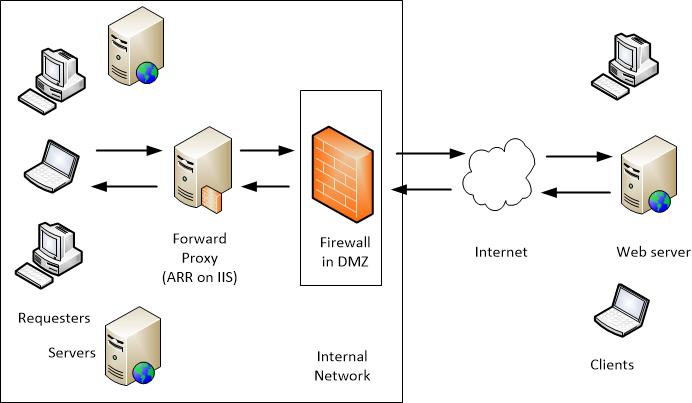
Before diving into the creation process, let’s clarify what a web proxy is and why you might need one. A web proxy server sits between your device and the websites you visit. When you request a webpage, your request first goes to the proxy server, which then fetches the page from the internet and sends it back to you. This process offers several benefits:
- Anonymity: Your IP address is hidden, making it harder for websites to track your location and browsing habits.
- Security: A web proxy can filter malicious content and block access to harmful websites.
- Bypass Restrictions: You can access content that might be blocked in your region or network.
- Caching: Proxies can cache frequently accessed content, improving loading times.
Creating a web proxy involves several approaches, each with its own advantages and disadvantages. We’ll explore some of the most common methods.
Method 1: Using a Web-Based Proxy
The simplest way to use a web proxy is through a web-based service. Numerous websites offer free or paid proxy services that allow you to browse the internet anonymously. These services are easy to use but may not offer the same level of security and control as other methods.
Steps to Use a Web-Based Proxy:
- Find a Reputable Web Proxy Site: Search online for “free web proxy” and choose a site with good reviews and a clear privacy policy.
- Enter the Website Address: On the proxy site, you’ll find a text box where you can enter the URL of the website you want to visit.
- Browse Anonymously: The proxy server will fetch the webpage and display it in your browser, masking your IP address.
While convenient, web-based proxies often suffer from slow speeds and may display ads. They also might not support secure (HTTPS) connections, leaving your data vulnerable. For more robust solutions, consider setting up your own proxy server.
Method 2: Setting Up a Proxy Server on Your Computer
For more control and security, you can set up a proxy server on your own computer. This involves installing proxy server software and configuring your browser or operating system to use the proxy. One popular option is using Squid, an open-source caching proxy.
Steps to Set Up a Proxy Server Using Squid:
- Install Squid: On Linux systems, you can typically install Squid using your distribution’s package manager (e.g.,
sudo apt-get install squidon Debian/Ubuntu). On Windows, you can download a pre-built Squid package. - Configure Squid: The main configuration file is usually located at
/etc/squid/squid.conf. You’ll need to edit this file to define access control lists (ACLs) and other settings. - Define ACLs: ACLs specify which IP addresses or networks are allowed to use the proxy. For example, to allow access from your local network, you might add lines like:
- Set HTTP Access: Configure Squid to listen on a specific port (e.g., 3128) by adding or modifying the
http_portdirective. - Restart Squid: After making changes to the configuration file, restart the Squid service to apply the changes (e.g.,
sudo systemctl restart squid). - Configure Your Browser: In your browser settings, specify the IP address and port of your proxy server. For example, if Squid is running on your local machine, the proxy address would be
127.0.0.1and the port would be3128.
acl localnet src 192.168.1.0/24
http_access allow localnetSetting up Squid requires some technical knowledge, but it offers a powerful and customizable proxy solution. You can configure Squid to cache web content, filter URLs, and perform other advanced functions.
Method 3: Using a Virtual Private Server (VPS) as a Proxy
Another option is to use a Virtual Private Server (VPS) as a proxy. This involves renting a VPS from a hosting provider and installing proxy server software on it. This method provides greater control and security compared to web-based proxies and allows you to bypass geographical restrictions more effectively.
Steps to Set Up a Proxy Server on a VPS:
- Choose a VPS Provider: Select a VPS provider that offers a reliable service and a suitable operating system (e.g., Linux).
- Set Up Your VPS: Follow the provider’s instructions to set up your VPS, including choosing a hostname and setting a strong password.
- Install Proxy Server Software: Install proxy server software like Squid or Shadowsocks on your VPS. The installation process is similar to setting up a proxy server on your local machine.
- Configure the Proxy Server: Configure the proxy server to listen on a specific port and define access control lists (ACLs).
- Secure Your Proxy Server: Implement security measures such as setting up a firewall (e.g., using
iptables) and regularly updating the proxy server software. - Connect to Your Proxy: Configure your browser or operating system to use the IP address and port of your VPS as a proxy.
Using a VPS as a proxy offers several advantages, including greater bandwidth, lower latency, and more control over security. However, it also requires more technical expertise and involves recurring costs.
Method 4: Using SSH Tunneling as a SOCKS Proxy
SSH tunneling provides a secure way to forward network traffic through an SSH connection. You can use SSH tunneling to create a SOCKS proxy, which allows you to route all your internet traffic through a remote server.
Steps to Create a SOCKS Proxy Using SSH Tunneling:
- Access to an SSH Server: You need access to an SSH server, such as a VPS or a remote computer.
- Establish an SSH Tunnel: Use the SSH command to create a tunnel that forwards traffic to a local port. For example:
- Configure Your Browser: In your browser settings, configure the SOCKS proxy to use
127.0.0.1as the host and1080as the port. - Browse Anonymously: All your internet traffic will now be routed through the SSH tunnel, masking your IP address and encrypting your data.
ssh -D 1080 user@remote_server_ipThis command creates a SOCKS proxy on your local machine, listening on port 1080. Replace user with your username on the remote server and remote_server_ip with the server’s IP address.
SSH tunneling is a simple and secure way to create a proxy, but it may not be as efficient as dedicated proxy server software. It’s best suited for occasional use or when you need a temporary proxy.
Considerations for Creating a Web Proxy
Before creating a web proxy, consider the following factors:
- Security: Ensure that your proxy server is properly secured to prevent unauthorized access and data breaches. Use strong passwords, implement a firewall, and keep your software up to date.
- Privacy: Understand the privacy policies of any third-party services you use, such as VPS providers or web-based proxies. Choose providers that respect your privacy and do not log your browsing activity.
- Performance: Consider the performance implications of using a proxy. Proxies can introduce latency and reduce browsing speeds. Choose a proxy server with sufficient bandwidth and processing power.
- Legality: Be aware of the legal implications of using a proxy. In some jurisdictions, using a proxy to bypass restrictions or access illegal content may be prohibited.
Choosing the Right Method
The best method for creating a web proxy depends on your specific needs and technical expertise. Web-based proxies are the simplest option for occasional use, while setting up a proxy server on your computer or a VPS offers more control and security. SSH tunneling provides a quick and secure way to create a temporary proxy. Consider your requirements carefully before choosing a method.
Conclusion
Creating a web proxy can significantly enhance your online privacy and security. By understanding the different methods and considerations involved, you can choose the best approach for your needs and take control of your online experience. Whether you opt for a simple web-based proxy or a more sophisticated VPS-based solution, a web proxy can provide an invaluable layer of protection in today’s digital landscape. Knowing how to create a web proxy is a valuable skill in protecting your online identity and accessing content freely.
[See also: Understanding Network Security]
[See also: How to Choose the Best VPN]
[See also: Protecting Your Online Privacy]
