Unveiling the Power of Internet Proxies: A Comprehensive Guide
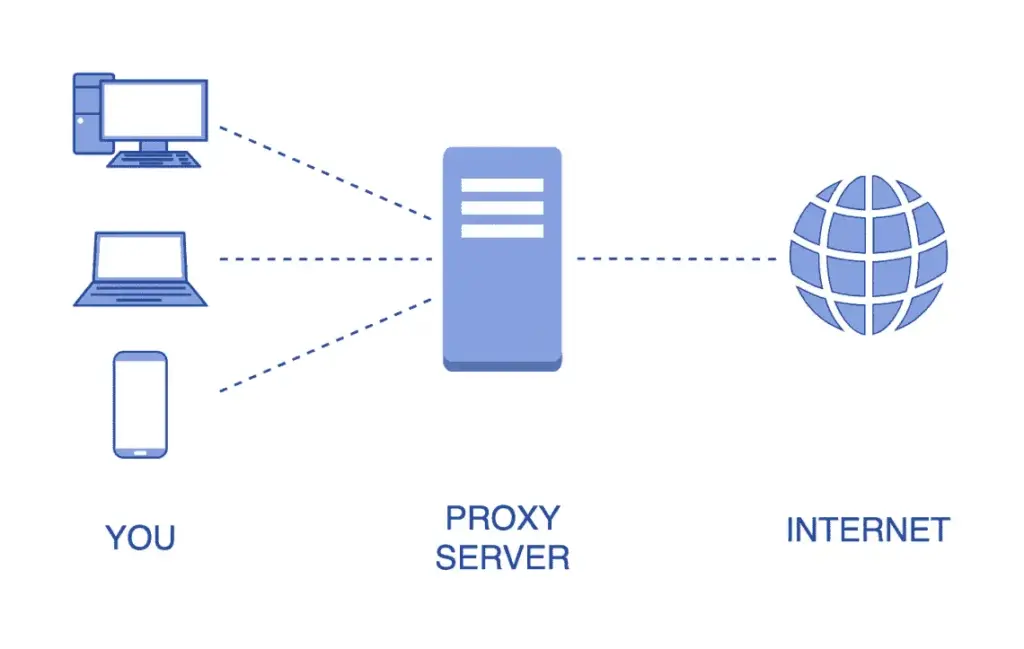
In today’s interconnected world, understanding the nuances of internet security and privacy is paramount. One crucial element in this landscape is the internet proxy. An internet proxy acts as an intermediary between your device and the internet. Instead of connecting directly to a website, your request first goes to the internet proxy server, which then forwards it to the destination. This simple yet powerful mechanism offers a range of benefits, from enhanced security and privacy to circumventing geographical restrictions. Let’s delve into the world of internet proxies and explore their functionalities, types, and applications.
What is an Internet Proxy?
At its core, an internet proxy is a server that sits between a user’s device and the internet. When a user makes a request to access a website or online service, the request is first routed through the internet proxy server. The internet proxy then forwards the request to the destination server, receives the response, and relays it back to the user. This process effectively masks the user’s IP address, making it appear as if the request originated from the internet proxy server itself.
How Internet Proxies Work
The functionality of an internet proxy can be broken down into several key steps:
- User Request: A user initiates a request to access a website or online service.
- Proxy Interception: The request is intercepted by the internet proxy server.
- Request Forwarding: The internet proxy server forwards the request to the destination server on behalf of the user.
- Response Reception: The destination server sends the response back to the internet proxy server.
- Response Delivery: The internet proxy server relays the response to the user.
This intermediary role allows internet proxies to perform various functions, including:
- IP Address Masking: Hiding the user’s real IP address to protect their identity and location.
- Content Filtering: Blocking access to specific websites or content based on predefined rules.
- Caching: Storing frequently accessed content to improve website loading speeds.
- Load Balancing: Distributing network traffic across multiple servers to prevent overload.
Types of Internet Proxies
Internet proxies come in various forms, each offering different levels of security, anonymity, and performance. Understanding the different types of internet proxies is crucial for choosing the right one for your specific needs.
HTTP Proxies
HTTP internet proxies are designed to handle HTTP (Hypertext Transfer Protocol) traffic, which is the standard protocol for web browsing. They are commonly used for accessing websites and downloading files. However, HTTP internet proxies do not encrypt traffic, making them less secure than other types of internet proxies.
HTTPS Proxies
HTTPS internet proxies, also known as SSL internet proxies, handle HTTPS (Hypertext Transfer Protocol Secure) traffic, which is an encrypted version of HTTP. They provide a higher level of security compared to HTTP internet proxies, as they encrypt the data transmitted between the user and the server. This encryption protects sensitive information from being intercepted by third parties. [See also: Understanding SSL Certificates]
SOCKS Proxies
SOCKS internet proxies are more versatile than HTTP and HTTPS internet proxies, as they can handle any type of network traffic, including HTTP, HTTPS, FTP, and SMTP. They operate at a lower level of the network stack, providing greater flexibility and control. SOCKS internet proxies are commonly used for applications that require a high degree of anonymity, such as online gaming and peer-to-peer file sharing.
Transparent Proxies
Transparent internet proxies, also known as intercepting internet proxies, are internet proxies that do not require any configuration on the user’s device. They are typically deployed by network administrators to monitor and control internet usage within an organization. Transparent internet proxies do not provide anonymity, as they reveal the user’s IP address to the destination server.
Anonymous Proxies
Anonymous internet proxies hide the user’s IP address but identify themselves as internet proxies. While they provide some level of anonymity, they are less effective at concealing the user’s identity than other types of internet proxies. Websites can often detect the use of anonymous internet proxies and block access.
Elite Proxies
Elite internet proxies, also known as highly anonymous internet proxies, provide the highest level of anonymity. They hide the user’s IP address and do not identify themselves as internet proxies. This makes it difficult for websites to detect the use of an elite internet proxy. Elite internet proxies are commonly used by individuals who require a high degree of privacy, such as journalists and activists.
Benefits of Using Internet Proxies
Using an internet proxy offers a range of benefits, including:
- Enhanced Security: Internet proxies can protect your device from malware and other online threats by filtering malicious content.
- Improved Privacy: Internet proxies can mask your IP address, making it more difficult for websites and online services to track your online activity.
- Access to Geo-Restricted Content: Internet proxies can allow you to access content that is blocked in your region by routing your traffic through a server located in a different country.
- Bypass Censorship: Internet proxies can help you bypass censorship by allowing you to access websites and online services that are blocked by your government or internet service provider.
- Improved Network Performance: Internet proxies can cache frequently accessed content, reducing bandwidth consumption and improving website loading speeds.
Use Cases for Internet Proxies
Internet proxies are used in a variety of settings, including:
- Personal Use: Individuals use internet proxies to protect their privacy, access geo-restricted content, and bypass censorship.
- Business Use: Businesses use internet proxies to improve network security, monitor employee internet usage, and conduct market research.
- Data Scraping: Data scientists use internet proxies to scrape data from websites without being blocked.
- Social Media Management: Social media marketers use internet proxies to manage multiple social media accounts without being flagged for suspicious activity.
Choosing the Right Internet Proxy
When choosing an internet proxy, it is important to consider your specific needs and requirements. Some factors to consider include:
- Security: Choose an internet proxy that offers strong encryption and protection against malware.
- Anonymity: Choose an internet proxy that provides the level of anonymity you require.
- Speed: Choose an internet proxy that offers fast and reliable performance.
- Location: Choose an internet proxy that has servers located in the regions you need to access content from.
- Cost: Internet proxies range in price from free to hundreds of dollars per month. Choose an internet proxy that fits your budget.
Potential Risks and Considerations
While internet proxies offer numerous benefits, it’s essential to be aware of potential risks:
- Free Proxies: Free internet proxies may collect your data or inject malware into your traffic. Exercise caution when using free internet proxies.
- Logging Policies: Some internet proxies log user activity, potentially compromising your privacy. Choose a internet proxy with a clear and transparent no-logs policy.
- Security Vulnerabilities: Internet proxies themselves can be vulnerable to security breaches. Ensure the internet proxy provider has robust security measures in place.
Conclusion
Internet proxies are a powerful tool for enhancing security, improving privacy, and accessing geo-restricted content. By understanding the different types of internet proxies and their respective benefits and risks, you can make informed decisions about which internet proxy is right for you. Whether you are an individual looking to protect your online privacy or a business seeking to improve network security, an internet proxy can be a valuable asset. Remember to choose a reputable internet proxy provider and prioritize security and privacy when making your selection.
