Unveiling the Power of Proxies: A Comprehensive Guide
In today’s interconnected digital landscape, the concept of a proxy server has become increasingly relevant. Whether you’re a cybersecurity professional, a business owner concerned with data security, or simply an individual seeking enhanced online privacy, understanding what a proxy is and how it functions is crucial. This comprehensive guide will delve into the intricacies of proxies, exploring their various types, benefits, and potential drawbacks. We will examine how proxies act as intermediaries between your device and the internet, masking your IP address and offering a range of advantages. This analysis will provide you with a solid foundation for making informed decisions about utilizing proxy services.
What is a Proxy Server?
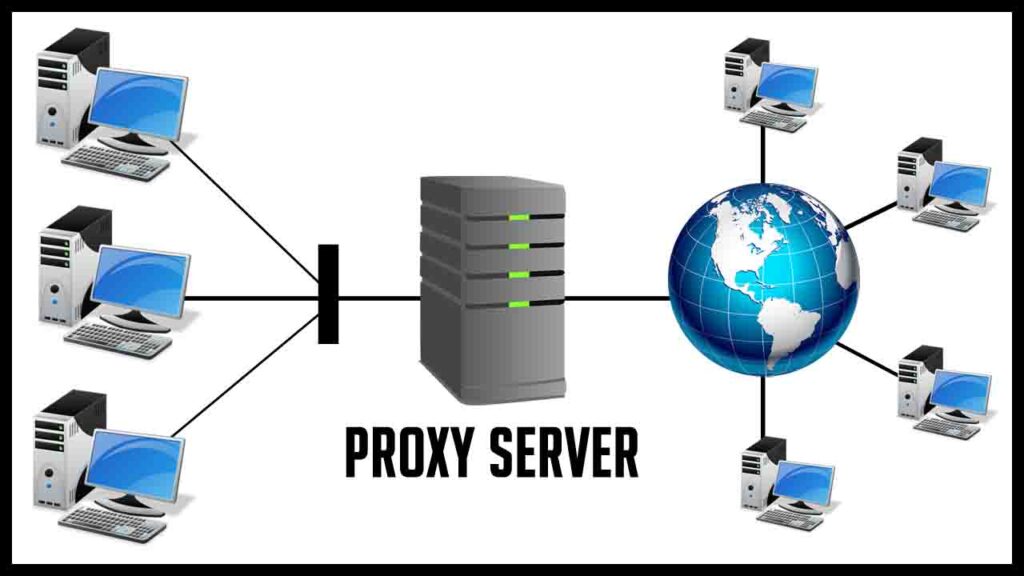
At its core, a proxy server acts as a gateway between you and the internet. Instead of connecting directly to a website or online service, your traffic is routed through the proxy server. This server then retrieves the requested information on your behalf and relays it back to you. Essentially, the proxy server acts as an intermediary, masking your IP address and location from the websites and services you access. This masking provides a layer of anonymity and can be used for various purposes, from bypassing geographical restrictions to enhancing online security.
Types of Proxy Servers
Proxy servers come in various forms, each offering different features and levels of security. Understanding the different types of proxies is essential for choosing the right solution for your needs.
HTTP Proxies
HTTP proxies are designed specifically for handling web traffic. They are commonly used for caching web pages to improve loading speeds and for filtering content. When you request a webpage through an HTTP proxy, the proxy server retrieves the page and stores a copy in its cache. If another user requests the same page, the proxy server can serve the cached version, reducing the load on the origin server and improving response times. However, HTTP proxies are not encrypted and are therefore not suitable for transmitting sensitive information.
HTTPS Proxies (SSL Proxies)
HTTPS proxies, also known as SSL proxies, provide an encrypted connection between your device and the proxy server. This encryption protects your data from eavesdropping and ensures that your communications are secure. HTTPS proxies are ideal for accessing sensitive websites and online services, such as banking portals and e-commerce sites. They are a crucial component of maintaining online privacy and security.
SOCKS Proxies
SOCKS proxies are more versatile than HTTP and HTTPS proxies. They can handle any type of traffic, including web traffic, email, and file transfers. SOCKS proxies operate at a lower level of the network stack, providing greater flexibility and control. They are often used for bypassing firewalls and accessing blocked content. SOCKS5, the latest version of the SOCKS protocol, supports authentication and encryption, further enhancing security. Using a SOCKS proxy can significantly improve your online experience.
Transparent Proxies
Transparent proxies intercept your traffic without your knowledge or consent. They are often used by organizations, such as schools and businesses, to monitor and filter internet usage. While transparent proxies can be useful for enforcing internet policies, they also raise privacy concerns. Users may not be aware that their traffic is being monitored, and their online activities may be tracked. It’s important to be aware of the presence of transparent proxies and to understand their implications for your privacy.
Reverse Proxies
Reverse proxies, unlike forward proxies, are deployed on the server-side. They sit in front of one or more web servers, intercepting incoming requests and distributing them to the appropriate server. Reverse proxies are commonly used for load balancing, caching, and security. They can improve the performance and reliability of web applications by distributing traffic across multiple servers and by caching frequently accessed content. Additionally, reverse proxies can protect web servers from attacks by filtering malicious traffic and hiding the server’s IP address.
Benefits of Using a Proxy Server
Using a proxy server offers a range of benefits, including enhanced privacy, improved security, and access to restricted content.
- Enhanced Privacy: Proxies mask your IP address, making it difficult for websites and online services to track your online activities.
- Improved Security: Proxies can filter malicious traffic and protect your device from cyber threats.
- Access to Restricted Content: Proxies can bypass geographical restrictions and allow you to access content that is blocked in your region.
- Load Balancing: Reverse proxies can distribute traffic across multiple servers, improving the performance and reliability of web applications.
- Caching: Proxies can cache frequently accessed content, reducing loading times and improving the user experience.
Potential Drawbacks of Using a Proxy Server
While proxy servers offer numerous benefits, they also have potential drawbacks. It’s important to be aware of these drawbacks before using a proxy service.
- Slower Connection Speeds: Routing your traffic through a proxy server can sometimes slow down your connection speed.
- Security Risks: Not all proxy servers are created equal. Some proxies may be insecure and could expose your data to cyber threats.
- Logging of Activity: Some proxy servers may log your online activity, which could compromise your privacy.
- Cost: High-quality proxy services often come with a cost. Free proxies may be unreliable and insecure.
Choosing the Right Proxy Server
Choosing the right proxy server depends on your specific needs and requirements. Consider the following factors when selecting a proxy service:
- Security: Choose a proxy server that offers strong encryption and security features.
- Speed: Select a proxy server that provides fast connection speeds.
- Reliability: Opt for a proxy server that is reliable and has a good uptime record.
- Location: Choose a proxy server that is located in a region that allows you to access the content you need.
- Cost: Consider your budget and choose a proxy service that offers the best value for your money.
How to Set Up a Proxy Server
Setting up a proxy server is relatively straightforward. The process varies depending on your operating system and web browser. In most cases, you will need to enter the proxy server’s IP address and port number in your device’s network settings or your browser’s settings. You can find instructions on how to set up a proxy server for your specific device and browser online. Ensure that you are using a reputable and secure proxy server to protect your data.
The Future of Proxies
As the internet continues to evolve, proxies will likely play an increasingly important role in online privacy and security. With growing concerns about data breaches and government surveillance, individuals and businesses are seeking ways to protect their online activities. Proxies offer a valuable tool for masking IP addresses, bypassing censorship, and enhancing security. The development of new proxy technologies and protocols will further enhance their capabilities and make them even more essential in the digital age. [See also: VPN vs. Proxy: Which is Right for You?] The ongoing debate about net neutrality and internet regulation will also likely influence the future of proxies. As governments and internet service providers seek to control online content and traffic, proxies may become even more critical for maintaining an open and accessible internet.
Conclusion
Proxy servers are a valuable tool for enhancing online privacy, improving security, and accessing restricted content. By understanding the different types of proxies and their benefits and drawbacks, you can make informed decisions about whether to use a proxy service. While proxies are not a perfect solution, they can provide an extra layer of protection and anonymity in an increasingly interconnected world. As the internet landscape continues to evolve, proxies will likely remain an important component of online security and privacy. Understanding how to use a proxy effectively is a crucial skill in today’s digital age, allowing individuals and businesses to navigate the internet with greater confidence and control. Before implementing any proxy solution, it is essential to thoroughly research and understand the specific features and security implications of the chosen service. With careful planning and implementation, proxies can be a powerful asset in protecting your online presence.
