Forward vs. Reverse Proxy: Understanding the Key Differences
In the world of network architecture and cybersecurity, proxies play a crucial role in managing traffic, enhancing security, and improving performance. Among the various types of proxies, forward and reverse proxies are two of the most common and essential. While both serve as intermediaries between clients and servers, they operate in fundamentally different ways. Understanding the difference between forward and reverse proxy configurations is crucial for designing robust and secure network infrastructures. This article delves into the intricacies of each, highlighting their distinct functionalities, use cases, and benefits.
What is a Forward Proxy?
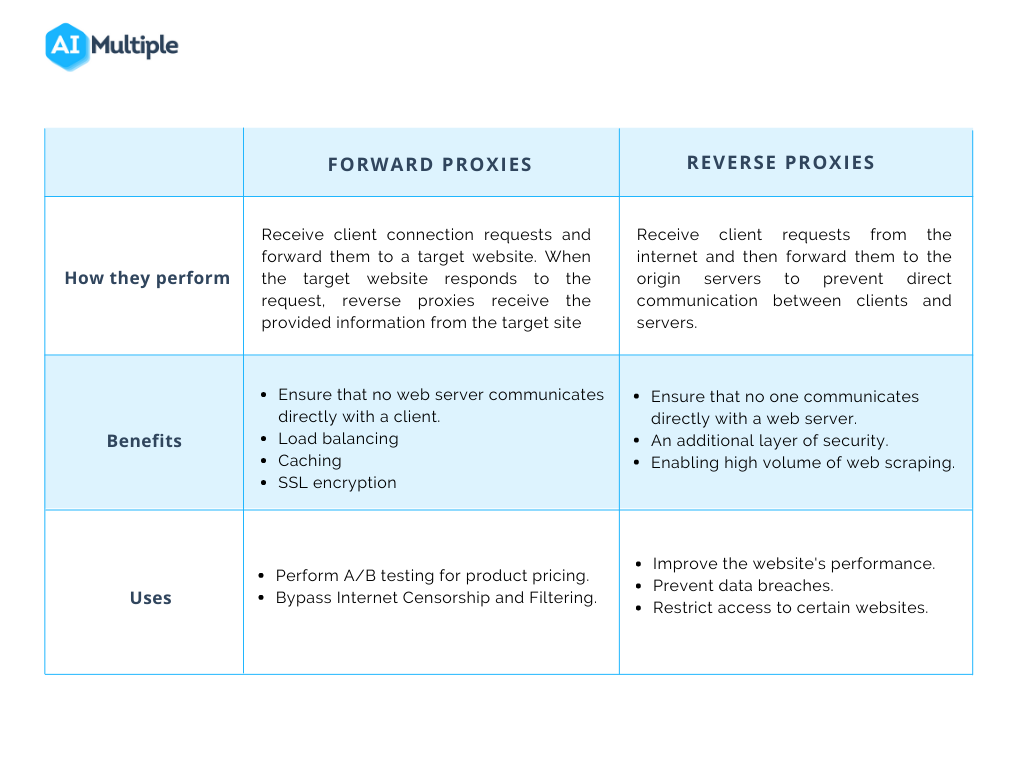
A forward proxy acts as an intermediary for clients requesting resources from various servers. Think of it as a gatekeeper standing between individual users and the internet. When a client makes a request, the forward proxy intercepts it, forwards the request to the destination server on behalf of the client, and then returns the response to the client. The destination server only sees the forward proxy’s IP address, effectively hiding the client’s IP address.
Key Characteristics of Forward Proxies
- Client-Side Intermediary: Primarily used to protect and manage client requests.
- Anonymity: Hides the client’s IP address, providing a degree of anonymity.
- Access Control: Can be configured to control which websites clients can access.
- Caching: Can cache frequently accessed content, reducing bandwidth usage and improving response times for clients.
- Security: Can filter malicious content and provide an additional layer of security for clients.
Use Cases for Forward Proxies
Forward proxies are commonly used in various scenarios, including:
- Bypassing Geographical Restrictions: Accessing content that is blocked in a specific region.
- Enhancing Privacy: Hiding the client’s IP address from websites.
- Content Filtering: Blocking access to certain types of websites or content.
- Improving Performance: Caching frequently accessed content to reduce latency.
- Network Security: Providing a centralized point for security policies and monitoring.
For example, a company might implement a forward proxy to prevent employees from accessing social media websites during work hours or to filter out potentially harmful content. Similarly, individuals might use a forward proxy to bypass geographical restrictions and access streaming services or news websites that are not available in their location. The difference between forward and reverse proxy becomes clear when considering who initiates the connection: in the case of a forward proxy, it’s the client.
What is a Reverse Proxy?
A reverse proxy, on the other hand, acts as an intermediary for servers, protecting them from direct exposure to clients. Instead of hiding the client’s IP address, it hides the identity and characteristics of the backend servers. When a client sends a request to a server, the reverse proxy intercepts it, forwards it to the appropriate backend server, and then returns the response to the client as if it came directly from the reverse proxy itself.
Key Characteristics of Reverse Proxies
- Server-Side Intermediary: Primarily used to protect and manage server requests.
- Load Balancing: Distributes client requests across multiple backend servers to prevent overload and ensure high availability.
- Security: Protects backend servers from direct exposure to the internet and potential attacks.
- Caching: Can cache frequently accessed content, reducing the load on backend servers and improving response times for clients.
- SSL Encryption: Can handle SSL encryption and decryption, offloading this task from backend servers.
Use Cases for Reverse Proxies
Reverse proxies are widely used in various scenarios, including:
- Load Balancing: Distributing traffic across multiple servers to handle high volumes of requests.
- Security: Protecting backend servers from DDoS attacks and other security threats.
- SSL Termination: Handling SSL encryption and decryption to improve server performance.
- Caching: Caching static content to reduce the load on backend servers.
- URL Rewriting: Simplifying URLs and improving SEO.
For instance, a large e-commerce website might use a reverse proxy to distribute traffic across multiple web servers, ensuring that the website remains responsive even during peak shopping seasons. The reverse proxy can also handle SSL encryption, freeing up the web servers to focus on processing requests. This highlights the critical difference between forward and reverse proxy – the latter protects the server.
Key Differences Between Forward and Reverse Proxies
The core difference between forward and reverse proxy configurations lies in their purpose and the entities they protect. Here’s a summary of the key distinctions:
- Direction of Traffic: A forward proxy handles outbound traffic from clients to the internet, while a reverse proxy handles inbound traffic from the internet to backend servers.
- Target Audience: A forward proxy is used by clients to protect their identity and access resources, while a reverse proxy is used by servers to protect their infrastructure and improve performance.
- Location in the Network: A forward proxy sits between clients and the internet, while a reverse proxy sits between the internet and backend servers.
- Visibility: Clients are aware that they are using a forward proxy, while they are typically unaware that they are interacting with a reverse proxy.
- Security Focus: Forward proxies focus on protecting clients from malicious content and privacy breaches, while reverse proxies focus on protecting servers from attacks and overload.
Another important difference between forward and reverse proxy is their configuration. Forward proxies often require explicit configuration on the client side, while reverse proxies are typically transparent to the client.
Benefits of Using Proxies
Both forward and reverse proxies offer significant benefits, depending on the specific use case. Here’s a brief overview of the advantages:
Benefits of Forward Proxies
- Enhanced Privacy: Hides the client’s IP address, providing anonymity.
- Improved Security: Filters malicious content and protects against online threats.
- Access Control: Allows administrators to control which websites clients can access.
- Bypassing Restrictions: Enables clients to bypass geographical restrictions and access blocked content.
- Caching: Improves performance by caching frequently accessed content.
Benefits of Reverse Proxies
- Load Balancing: Distributes traffic across multiple servers, ensuring high availability and performance.
- Enhanced Security: Protects backend servers from direct exposure to the internet and potential attacks.
- SSL Termination: Handles SSL encryption and decryption, offloading this task from backend servers.
- Caching: Reduces the load on backend servers by caching static content.
- Simplified Management: Provides a centralized point for managing server configurations and security policies.
Understanding the difference between forward and reverse proxy configurations allows organizations to leverage the right tool for their specific needs, whether it’s protecting client privacy or ensuring server availability.
Implementing Forward and Reverse Proxies
Implementing forward and reverse proxies requires careful planning and configuration. Several popular software solutions are available for both types of proxies.
Forward Proxy Implementation
Common software for implementing forward proxies includes:
- Squid: A widely used open-source caching and forwarding HTTP web proxy.
- Privoxy: A privacy-enhancing proxy that filters out ads and other unwanted content.
- CCProxy: A Windows-based proxy server that offers features like internet access control and bandwidth management.
Configuration typically involves setting up the proxy server on a dedicated machine and configuring client devices to use the proxy server. [See also: Network Security Best Practices]
Reverse Proxy Implementation
Popular software for implementing reverse proxies includes:
- Nginx: A high-performance web server and reverse proxy that is widely used for load balancing and caching.
- Apache HTTP Server: A popular web server that can also be configured as a reverse proxy.
- HAProxy: A reliable, high-performance TCP/HTTP load balancer that is often used as a reverse proxy.
Configuration involves setting up the reverse proxy server in front of the backend servers and configuring it to forward requests to the appropriate servers. The difference between forward and reverse proxy setup is crucial for correct operation.
Conclusion
In summary, the difference between forward and reverse proxy servers is significant. Forward proxies protect clients by hiding their IP addresses and controlling their access to the internet, while reverse proxies protect servers by hiding their identities and distributing traffic. Understanding these distinctions is essential for designing secure and efficient network architectures. By leveraging the appropriate type of proxy, organizations can enhance security, improve performance, and simplify network management. Choosing the right proxy depends on the specific needs and goals of the organization. Whether it’s enhancing client privacy or ensuring server availability, proxies play a vital role in today’s complex network environments. The practical difference between forward and reverse proxy implementations can significantly impact network security and performance. Properly configured proxies are invaluable tools for any organization seeking to optimize its network infrastructure. So, the next time you hear about proxies, remember the fundamental difference between forward and reverse proxy and how each contributes to a more secure and efficient online experience. Recognizing this difference between forward and reverse proxy is key to effective network management. The strategic deployment of either a forward or reverse proxy, or even both, can greatly enhance your overall network security posture. Further understanding the difference between forward and reverse proxy leads to better network design and resource allocation. Knowing the difference between forward and reverse proxy is essential for any IT professional. The subtle but important difference between forward and reverse proxy can have a big impact on network performance. The key difference between forward and reverse proxy lies in who they protect. The functional difference between forward and reverse proxy is what makes them so valuable. The conceptual difference between forward and reverse proxy is easy to grasp once you understand their roles.
