Mastering Linux HTTP Proxy: A Comprehensive Guide
In today’s interconnected world, understanding how to manage network traffic is crucial for both individual users and organizations. A Linux HTTP proxy server acts as an intermediary between your computer and the internet, providing enhanced security, privacy, and control over web access. This comprehensive guide will delve into the intricacies of setting up, configuring, and utilizing a Linux HTTP proxy, empowering you to optimize your network experience.
What is an HTTP Proxy?
Before diving into the specifics of Linux HTTP proxy servers, let’s define what an HTTP proxy is. An HTTP proxy is a server that sits between a client (e.g., a web browser) and a web server. When a client requests a resource from a web server, the request is first sent to the proxy server. The proxy server then forwards the request to the web server on behalf of the client. The web server responds to the proxy server, which then forwards the response back to the client.
This intermediary role allows the proxy server to perform various functions, including:
- Caching: Storing frequently accessed web content to improve performance and reduce bandwidth usage.
- Filtering: Blocking access to specific websites or content based on predefined rules.
- Security: Masking the client’s IP address to protect privacy and prevent direct attacks.
- Logging: Tracking web traffic for auditing and monitoring purposes.
- Bypassing Restrictions: Accessing content that may be geographically restricted.
Why Use a Linux HTTP Proxy?
Using a Linux HTTP proxy offers several advantages, especially in environments where control and security are paramount:
- Cost-Effectiveness: Linux is an open-source operating system, making it a cost-effective solution for setting up a proxy server.
- Flexibility: Linux provides a high degree of customization, allowing you to tailor the proxy server to your specific needs.
- Security: Linux is known for its robust security features, making it a reliable platform for securing your network traffic.
- Scalability: Linux can handle a large volume of traffic, making it suitable for both small and large networks.
- Control: You have complete control over the proxy server’s configuration and behavior.
Popular Linux HTTP Proxy Servers
Several HTTP proxy server software options are available for Linux. Here are some of the most popular:
- Squid: A high-performance caching and forwarding HTTP web proxy. It’s widely used in corporate environments and offers advanced features like access control lists (ACLs) and content filtering.
- Privoxy: A non-caching web proxy with advanced privacy features. It’s designed to protect your privacy by filtering web pages and removing unwanted content like ads and trackers.
- Tinyproxy: A lightweight HTTP proxy server that’s easy to configure and use. It’s suitable for small networks and personal use.
- Apache: While primarily a web server, Apache can also be configured as a reverse proxy or a forward proxy using modules like `mod_proxy`.
- Nginx: Similar to Apache, Nginx is a high-performance web server that can also function as a proxy server.
Setting Up a Linux HTTP Proxy with Squid
Let’s walk through the process of setting up a Linux HTTP proxy server using Squid, a popular and powerful option. This example assumes you are using a Debian-based distribution like Ubuntu.
Installation
First, update your package lists and install Squid:
sudo apt update
sudo apt install squid
Configuration
The main configuration file for Squid is located at `/etc/squid/squid.conf`. Before making any changes, it’s a good practice to back up the original file:
sudo cp /etc/squid/squid.conf /etc/squid/squid.conf.backup
Now, open the configuration file with your favorite text editor (e.g., nano or vim):
sudo nano /etc/squid/squid.conf
Here are some essential configuration options:
- `http_port`: Specifies the port Squid listens on. The default is 3128.
- `acl`: Defines access control lists (ACLs) to control who can use the proxy server.
- `http_access`: Specifies the rules for allowing or denying access based on the ACLs.
For example, to allow access from your local network (192.168.1.0/24), add the following lines to the configuration file:
acl localnet src 192.168.1.0/24
http_access allow localnet
http_access deny all
This configuration defines an ACL named `localnet` that matches traffic from the 192.168.1.0/24 network. It then allows access for this network and denies access for all other traffic. Remember to customize the `acl` to match your network configuration.
Restarting Squid
After making changes to the configuration file, you need to restart Squid for the changes to take effect:
sudo systemctl restart squid
You can check the status of Squid to ensure it’s running correctly:
sudo systemctl status squid
Firewall Configuration
If you have a firewall enabled, you need to allow traffic to the Squid port (3128 by default). For example, if you’re using UFW, you can use the following command:
sudo ufw allow 3128
Configuring Clients to Use the Proxy
Once the Linux HTTP proxy server is set up, you need to configure your client devices (e.g., web browsers) to use it. The configuration process varies depending on the client application.
Web Browsers
Most web browsers allow you to configure a proxy server in their settings. For example, in Firefox, you can go to Options > General > Network Settings > Settings and enter the proxy server’s IP address and port number.
Command Line
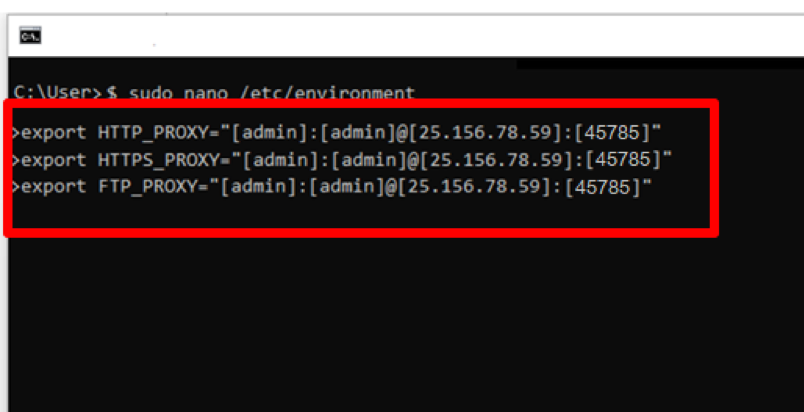
You can also configure the proxy server for command-line tools using environment variables. For example, you can set the `http_proxy` and `https_proxy` environment variables:
export http_proxy="http://proxy_server_ip:3128"
export https_proxy="http://proxy_server_ip:3128"
Replace `proxy_server_ip` with the actual IP address of your Linux HTTP proxy server.
Advanced Configuration
Squid offers a wide range of advanced configuration options. Here are a few examples:
- Caching Hierarchy: Configuring Squid to use a caching hierarchy to improve performance.
- Content Filtering: Using Squid’s ACLs to filter web content based on keywords or categories.
- Authentication: Requiring users to authenticate before using the proxy server.
- SSL Bumping: Intercepting and inspecting SSL/TLS traffic (use with caution due to privacy implications).
These advanced features require a deeper understanding of Squid’s configuration options. Refer to the Squid documentation for more information.
Troubleshooting
If you encounter problems with your Linux HTTP proxy server, here are some troubleshooting tips:
- Check the Squid logs: The Squid logs are located at `/var/log/squid/access.log` and `/var/log/squid/cache.log`. These logs can provide valuable information about errors and issues.
- Verify the configuration file: Double-check the `squid.conf` file for any syntax errors or incorrect settings.
- Test the connection: Use tools like `curl` or `wget` to test the connection to the proxy server.
- Check the firewall: Ensure that the firewall is not blocking traffic to the Squid port.
Security Considerations
When setting up a Linux HTTP proxy server, it’s essential to consider security implications. Here are some best practices:
- Keep the software up to date: Regularly update Squid and other software to patch security vulnerabilities.
- Restrict access: Limit access to the proxy server to authorized users and networks.
- Use strong passwords: If you’re using authentication, use strong passwords for all user accounts.
- Monitor the logs: Regularly monitor the Squid logs for suspicious activity.
- Consider using HTTPS: If you’re handling sensitive data, consider using HTTPS to encrypt traffic between the client and the proxy server.
Conclusion
Setting up a Linux HTTP proxy server can provide significant benefits in terms of security, privacy, and control over web access. By understanding the concepts and following the steps outlined in this guide, you can effectively manage your network traffic and optimize your online experience. Whether you’re a home user looking to protect your privacy or a network administrator managing a large corporate network, a Linux HTTP proxy is a valuable tool to have in your arsenal. Remember to always prioritize security and keep your software up to date to ensure the ongoing protection of your network.
A properly configured Linux HTTP proxy can be a powerful asset for any network. Understanding its capabilities and limitations is key to maximizing its potential. As technology evolves, so too will the methods and best practices surrounding proxy servers. Stay informed and adapt your configurations as needed to maintain a secure and efficient network environment. By leveraging the flexibility and power of Linux, you can create a customized proxy solution that meets your specific needs and enhances your overall online experience. The Linux HTTP proxy provides a robust and adaptable solution for managing web traffic in a variety of environments.
[See also: Setting Up a Firewall on Linux]
[See also: Introduction to Network Security]
