Navigating the Web Anonymously: Choosing Good Proxies to Use
In today’s digital landscape, online privacy and security are paramount. Whether you’re conducting market research, managing social media accounts, or simply seeking to browse the internet without being tracked, using a proxy server can be an invaluable tool. A proxy server acts as an intermediary between your device and the internet, masking your IP address and providing an extra layer of anonymity. However, not all proxies are created equal. Choosing the right one is crucial for ensuring both security and performance. This article delves into the world of proxies, exploring what makes them ‘good,’ the different types available, and how to select the best option for your specific needs. The goal is to provide a clear understanding of what constitutes good proxies to use, and empower you to make informed decisions when choosing a proxy service.
Understanding Proxy Servers
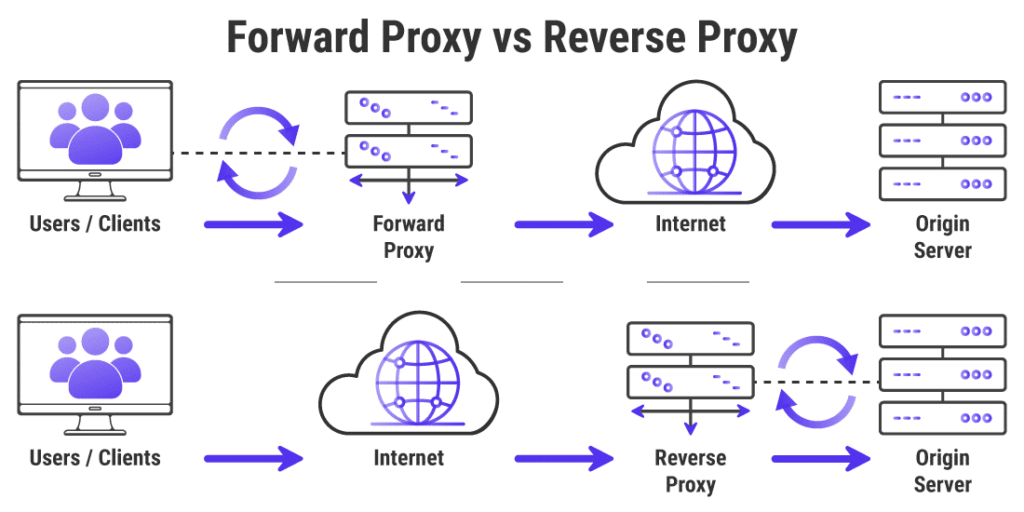
At its core, a proxy server is a computer that sits between your computer and the internet. When you send a request to a website, it first goes to the proxy server, which then forwards the request to the website on your behalf. The website sees the proxy server’s IP address, not yours. This process effectively hides your IP address, making it more difficult for websites and third parties to track your online activity. Good proxies to use offer a balance between anonymity, speed, and reliability.
Why Use a Proxy Server?
- Privacy: Hides your IP address, making it harder to track your online activities.
- Security: Adds a layer of protection against malicious websites and cyber threats.
- Access Restricted Content: Bypasses geographical restrictions and censorship.
- Improved Speed and Bandwidth: Caches frequently accessed content, leading to faster loading times.
- Load Balancing: Distributes network traffic across multiple servers, preventing overload.
Types of Proxy Servers
There are several types of proxy servers, each offering different levels of security, anonymity, and performance. Understanding these differences is essential when selecting good proxies to use.
HTTP Proxies
HTTP proxies are designed specifically for web traffic. They handle HTTP and HTTPS requests and are commonly used for browsing the web. While they offer a basic level of anonymity, they are not as secure as other types of proxies. They are often used for accessing geo-restricted content or bypassing basic website filters.
SOCKS Proxies
SOCKS (Socket Secure) proxies are more versatile than HTTP proxies. They can handle any type of network traffic, including email, FTP, and peer-to-peer connections. SOCKS proxies provide a higher level of anonymity because they don’t disclose the type of traffic they are handling. SOCKS5 is the latest version and offers the best security and performance.
Transparent Proxies
Transparent proxies identify themselves as proxies and may even pass along your IP address to the destination server. They are often used by organizations to monitor and control internet usage. Transparent proxies offer little to no anonymity and are not ideal for users seeking privacy.
Anonymous Proxies
Anonymous proxies hide your IP address but still identify themselves as proxies. While they offer better anonymity than transparent proxies, they are not completely untraceable. Websites can still detect that you are using a proxy, which may lead to restrictions or blocked access.
Elite Proxies (Highly Anonymous Proxies)
Elite proxies, also known as highly anonymous proxies, provide the highest level of anonymity. They hide your IP address and do not identify themselves as proxies. Websites cannot detect that you are using a proxy, making it virtually impossible to trace your online activity. Elite proxies are the preferred choice for users who require maximum privacy and security.
Factors to Consider When Choosing a Proxy
Selecting good proxies to use involves considering several factors. Here are some key aspects to keep in mind:
Anonymity Level
Determine the level of anonymity you require. If you need maximum privacy, opt for elite proxies. If basic anonymity is sufficient, anonymous or HTTP proxies may suffice. Avoid transparent proxies if privacy is a concern.
Speed and Reliability
A slow or unreliable proxy can significantly impact your browsing experience. Look for proxies that offer fast connection speeds and minimal downtime. Consider testing the proxy’s performance before committing to a long-term subscription.
Location
The location of the proxy server can affect your ability to access geo-restricted content. Choose a proxy server located in the region where the content is available. Some proxy providers offer servers in multiple locations, allowing you to switch between them as needed.
Security
Ensure that the proxy server uses encryption to protect your data from interception. SOCKS5 proxies offer strong encryption and are generally more secure than HTTP proxies. Also, consider the reputation of the proxy provider and their security practices.
Cost
Proxy services range in price from free to hundreds of dollars per month. Free proxies are often unreliable and may compromise your security. Paid proxies typically offer better performance, security, and customer support. Evaluate your budget and choose a proxy service that provides the best value for your needs.
Where to Find Good Proxies
Finding good proxies to use requires careful research and evaluation. Here are some resources to help you in your search:
Proxy Provider Websites
Many websites specialize in providing proxy services. These providers offer a range of proxy types and subscription plans. Look for providers with positive reviews and a proven track record of reliability and security. Some popular providers include Smartproxy, Oxylabs, and Bright Data.
Proxy Lists
Proxy lists are websites that compile lists of publicly available proxy servers. While these lists can be a convenient way to find free proxies, they often contain outdated or unreliable proxies. Use proxy lists with caution and be aware of the potential security risks.
Proxy Checker Tools
Proxy checker tools allow you to test the functionality and anonymity of a proxy server. These tools can help you identify proxies that are working and provide information about their location, speed, and anonymity level. Use proxy checker tools to verify the quality of proxies before using them.
Potential Risks and Considerations
While good proxies to use can enhance your online privacy and security, it’s essential to be aware of the potential risks and considerations:
Security Risks
Using unreliable or compromised proxies can expose your data to security risks. Free proxies are particularly vulnerable to malware and data theft. Always use reputable proxy providers and ensure that the proxy server uses encryption.
Logging
Some proxy servers may log your IP address and browsing activity. This information can be used to track your online behavior or even sold to third parties. Choose a proxy provider with a clear and transparent privacy policy that prohibits logging.
Performance Issues
Poorly configured or overloaded proxies can lead to slow connection speeds and frequent downtime. Test the performance of a proxy server before using it for critical tasks. Consider upgrading to a paid proxy service if you experience persistent performance issues.
Legal Considerations
Using proxies to bypass geographical restrictions or access illegal content may violate the terms of service of websites or even be illegal in some jurisdictions. Be aware of the legal implications of using proxies and avoid engaging in any unlawful activities.
Best Practices for Using Proxies
To maximize the benefits of using proxies while minimizing the risks, follow these best practices:
- Choose a Reputable Provider: Select a proxy provider with a proven track record of reliability, security, and customer support.
- Use Encryption: Ensure that the proxy server uses encryption to protect your data from interception.
- Monitor Performance: Regularly monitor the performance of the proxy server and switch to a different proxy if you experience persistent issues.
- Update Software: Keep your operating system, browser, and other software up to date to protect against security vulnerabilities.
- Use a VPN: Consider using a VPN in conjunction with a proxy server for enhanced security and anonymity.
Conclusion
Choosing good proxies to use is a crucial step in protecting your online privacy and security. By understanding the different types of proxies, considering the key factors, and following best practices, you can find a proxy server that meets your specific needs and enhances your online experience. Whether you’re conducting market research, managing social media accounts, or simply browsing the web, a well-chosen proxy can provide the anonymity and security you need to navigate the digital world with confidence. Remember to prioritize security, reliability, and performance when selecting a proxy service, and always be aware of the potential risks and legal considerations. With the right approach, you can leverage the power of proxies to protect your online identity and access the content you need, wherever you are in the world. Always make sure to research and validate any proxy service before committing to it. [See also: How to Choose the Right Proxy Service] [See also: Best Proxy Providers of 2024] [See also: Understanding Proxy Server Security Risks]
