Proxy Mean: Understanding Its Function, Types, and Security Implications
In the digital age, online privacy and security are paramount. One of the tools frequently employed to enhance these aspects is a proxy server. But what does “proxy mean” in the context of internet usage? This article delves into the intricacies of proxy servers, exploring their functions, different types, and the security implications they carry. Understanding the proxy mean is crucial for anyone looking to navigate the internet safely and efficiently.
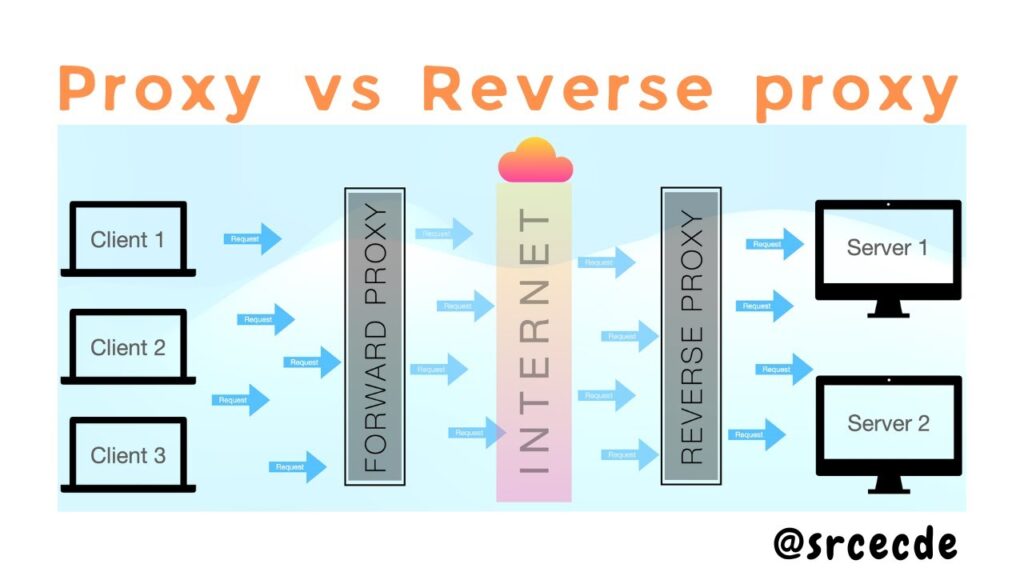
What Does Proxy Mean? A Detailed Explanation
At its core, a proxy acts as an intermediary between your device and the internet. When you connect to the internet without a proxy, your device directly communicates with the websites and services you access. This reveals your IP address, location, and other identifying information. A proxy server, however, masks your IP address with its own, making it appear as though the connection is originating from the proxy server itself. This indirection offers several benefits, including enhanced privacy, access to geo-restricted content, and improved network performance.
Simply put, the proxy mean refers to its function as a go-between, handling requests on behalf of the user. This fundamental role allows for a layer of abstraction that can be leveraged for various purposes.
Functions of a Proxy Server
Privacy and Anonymity
One of the primary functions of a proxy server is to provide privacy and anonymity. By masking your IP address, it becomes more difficult for websites and online services to track your online activities. This is particularly useful for individuals concerned about their digital footprint and potential surveillance.
Accessing Geo-Restricted Content
Many websites and streaming services restrict access based on geographical location. A proxy server located in a different region can bypass these restrictions, allowing you to access content that would otherwise be unavailable. For example, a user in Europe could use a US-based proxy to access American streaming services.
Improved Network Performance
Some proxy servers cache frequently accessed content, such as images and videos. When you request this content, the proxy server can deliver it from its cache, reducing latency and improving network performance. This is particularly beneficial for organizations with many users accessing the same online resources.
Bypassing Censorship
In countries with strict internet censorship, proxy servers can be used to bypass government restrictions and access blocked websites and services. This allows individuals to access information and express their opinions freely, even in censored environments.
Security Enhancement
A proxy server can act as a buffer between your device and the internet, protecting you from malicious websites and cyberattacks. Some proxy servers include built-in security features, such as malware scanning and content filtering, which can help to prevent security breaches. However, not all proxies are created equal, and some can pose significant security risks.
Types of Proxy Servers
Understanding the different types of proxy servers is crucial for choosing the right one for your needs.
HTTP Proxies
HTTP proxies are designed specifically for handling HTTP traffic, which is the standard protocol for web browsing. They are commonly used to access websites and web-based applications. HTTP proxies are relatively simple to set up and use, but they may not be suitable for all types of internet traffic.
HTTPS Proxies
HTTPS proxies are similar to HTTP proxies, but they provide an additional layer of security by encrypting the traffic between your device and the proxy server. This helps to protect your data from eavesdropping and interception. HTTPS proxies are recommended for accessing sensitive websites and services, such as online banking and e-commerce platforms.
SOCKS Proxies
SOCKS proxies are more versatile than HTTP and HTTPS proxies, as they can handle any type of internet traffic, including email, file transfer, and streaming media. SOCKS proxies operate at a lower level of the network stack, making them more flexible and adaptable. They are commonly used for bypassing firewalls and accessing blocked services.
Transparent Proxies
Transparent proxies, also known as intercepting proxies, are typically deployed by organizations to monitor and control internet usage. They operate without the user’s knowledge or consent, and they can be used to filter content, track browsing history, and enforce security policies. Transparent proxies are often used in schools, workplaces, and public Wi-Fi networks.
Anonymous Proxies
Anonymous proxies are designed to hide your IP address and provide a degree of anonymity. However, they may not encrypt your traffic, which means that your data can still be intercepted. Anonymous proxies are suitable for basic privacy needs, but they may not be sufficient for sensitive activities.
Elite Proxies
Elite proxies are the most secure and anonymous type of proxy server. They not only hide your IP address but also prevent websites from detecting that you are using a proxy. This makes it much more difficult to track your online activities. Elite proxies are recommended for users who require the highest level of privacy and security.
Security Implications of Using Proxy Servers
While proxy servers can enhance your online privacy and security, they also come with certain risks. It’s essential to be aware of these risks and take appropriate precautions to protect yourself.
Malicious Proxies
Some proxy servers are operated by malicious actors who may attempt to steal your data, install malware on your device, or redirect you to phishing websites. It’s crucial to choose a reputable proxy provider and avoid using free or untrusted proxies. Always check reviews and ensure the proxy service has a strong reputation for security.
Data Logging
Many proxy servers log user data, including IP addresses, browsing history, and other sensitive information. This data can be used for various purposes, such as targeted advertising, identity theft, and surveillance. Before using a proxy server, carefully review its privacy policy to understand how your data is collected, stored, and used.
Man-in-the-Middle Attacks
If you use a non-encrypted proxy server, your traffic can be intercepted by malicious actors who can then steal your data or inject malicious code into your browsing session. This is known as a man-in-the-middle attack. To protect yourself, always use an HTTPS proxy or a VPN (Virtual Private Network) when accessing sensitive websites and services.
Performance Issues
Some proxy servers can slow down your internet connection, especially if they are located far away from your physical location or if they are overloaded with traffic. This can lead to a frustrating browsing experience. Before committing to a proxy service, test its performance to ensure that it meets your needs. The proxy mean should involve an improvement, not a hindrance, to your browsing experience.
Choosing the Right Proxy Server
Selecting the right proxy server depends on your specific needs and priorities. Consider the following factors when making your decision:
- Security: Choose a proxy server that offers strong encryption and data protection measures.
- Anonymity: If anonymity is important to you, opt for an elite proxy that hides your IP address and prevents websites from detecting that you are using a proxy.
- Performance: Test the performance of the proxy server to ensure that it provides a fast and reliable connection.
- Location: Choose a proxy server located in a region that allows you to access the content you need.
- Price: Free proxies may be tempting, but they often come with security risks and performance issues. Consider paying for a reputable proxy service that offers better security and reliability.
By carefully considering these factors, you can choose a proxy server that meets your needs and protects your online privacy and security. Understanding what a proxy means and how it functions is the first step in making an informed decision.
Conclusion
Understanding the proxy mean and how proxies function is essential for navigating the internet safely and efficiently. From providing anonymity and accessing geo-restricted content to enhancing network performance and bypassing censorship, proxy servers offer a wide range of benefits. However, it’s crucial to be aware of the security implications and choose a reputable proxy provider to mitigate potential risks. By carefully evaluating your needs and selecting the right type of proxy server, you can leverage this powerful tool to enhance your online experience and protect your digital privacy. Remember to always prioritize security and choose proxies from trusted sources to avoid potential harm.
[See also: What is a VPN and How Does it Work?]
[See also: The Importance of Online Privacy in 2024]
[See also: How to Secure Your Home Network]
