SSL Packet Inspection: Understanding the Risks and Benefits
In today’s digital landscape, securing online communications is paramount. Secure Sockets Layer (SSL) packet inspection, also known as Transport Layer Security (TLS) inspection, plays a crucial role in many organizations’ security strategies. But what exactly is SSL packet inspection, and what are the associated risks and benefits? This article provides a comprehensive overview of SSL packet inspection, exploring its functionality, advantages, disadvantages, and best practices.
What is SSL Packet Inspection?
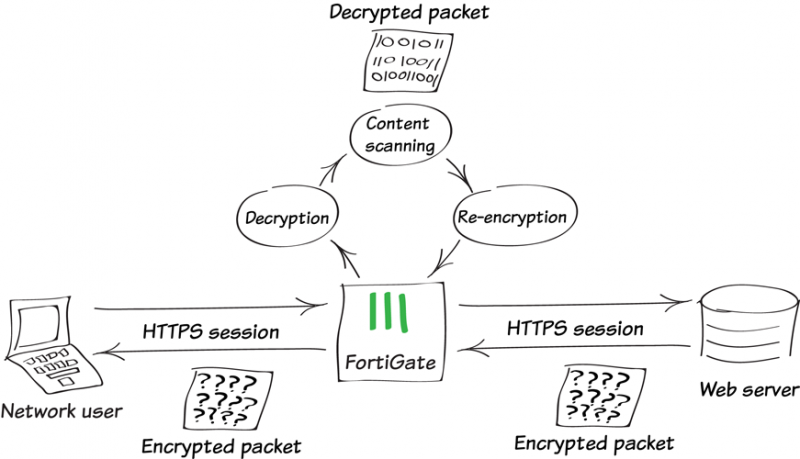
SSL packet inspection involves decrypting encrypted network traffic to analyze its content. When data is transmitted using SSL/TLS, it’s encrypted to protect its confidentiality. Traditional security devices, like firewalls and intrusion detection systems (IDS), cannot directly inspect this encrypted traffic. SSL packet inspection addresses this limitation by intercepting the encrypted traffic, decrypting it, analyzing its content for malicious activity, and then re-encrypting it before forwarding it to its destination. This process is often referred to as “man-in-the-middle” (MITM) inspection, although in this controlled environment, it’s a deliberate security measure performed by a trusted device.
The primary goal of SSL packet inspection is to identify and block threats that may be hidden within encrypted traffic. Malware, data exfiltration attempts, and other malicious activities can be concealed using SSL/TLS encryption, making it difficult for traditional security measures to detect them. By decrypting and inspecting the traffic, organizations can gain visibility into the content and identify potential threats.
How SSL Packet Inspection Works
The SSL packet inspection process typically involves the following steps:
- Interception: The security device intercepts the encrypted SSL/TLS traffic.
- Decryption: The device decrypts the traffic using the server’s private key (or a key that the organization has configured for this purpose). This step requires the organization to have access to the necessary decryption keys.
- Inspection: The decrypted traffic is then inspected for malicious content, such as malware, viruses, or data exfiltration attempts. This inspection may involve signature-based detection, behavioral analysis, or other advanced threat detection techniques.
- Re-encryption: After inspection, the traffic is re-encrypted using the server’s public key (or a new key generated by the inspection device).
- Forwarding: The re-encrypted traffic is then forwarded to its intended destination.
Benefits of SSL Packet Inspection
Implementing SSL packet inspection offers several significant benefits:
- Enhanced Threat Detection: By decrypting and inspecting encrypted traffic, organizations can identify and block threats that would otherwise be hidden.
- Improved Data Loss Prevention (DLP): SSL packet inspection can help prevent sensitive data from being exfiltrated from the network by inspecting encrypted traffic for confidential information.
- Compliance: Some regulatory compliance standards require organizations to inspect encrypted traffic for specific types of data or activity. SSL packet inspection can help organizations meet these requirements.
- Application Control: It allows organizations to enforce policies regarding the use of specific applications, even when those applications use encryption.
- Visibility into Encrypted Traffic: Provides a comprehensive view of what’s happening within encrypted communications, which is crucial for incident response and threat hunting.
Risks and Challenges of SSL Packet Inspection
While SSL packet inspection offers numerous benefits, it also presents several risks and challenges:
- Performance Impact: Decrypting and inspecting encrypted traffic can be resource-intensive, which can impact network performance. Organizations need to ensure that their security devices have sufficient processing power to handle the traffic volume.
- Privacy Concerns: SSL packet inspection involves decrypting and inspecting user data, which raises privacy concerns. Organizations need to be transparent with users about their inspection practices and ensure that they are complying with all applicable privacy regulations.
- Complexity: Implementing and managing SSL packet inspection can be complex, requiring specialized expertise.
- Certificate Management: SSL packet inspection requires the organization to manage certificates to ensure that the re-encrypted traffic is trusted by the client. Improper certificate management can lead to browser warnings and other security issues.
- Legal and Ethical Considerations: There are legal and ethical considerations surrounding the interception and decryption of user data. Organizations need to ensure that they have the legal authority to perform SSL packet inspection and that they are doing so in an ethical manner.
- Browser Compatibility Issues: Some older browsers may not be compatible with SSL packet inspection, which can lead to connectivity problems.
Best Practices for Implementing SSL Packet Inspection
To mitigate the risks and challenges associated with SSL packet inspection, organizations should follow these best practices:
- Develop a Clear Policy: Organizations should develop a clear policy outlining the purpose, scope, and limitations of their SSL packet inspection practices. This policy should be communicated to users and should be consistent with all applicable laws and regulations.
- Choose the Right Tools: Organizations should select security devices that are specifically designed for SSL packet inspection and that can handle the expected traffic volume.
- Implement Certificate Management: Organizations should implement a robust certificate management system to ensure that the re-encrypted traffic is trusted by clients. This system should include procedures for generating, distributing, and revoking certificates.
- Monitor Performance: Organizations should monitor network performance to ensure that SSL packet inspection is not negatively impacting user experience.
- Provide User Education: Users should be educated about the organization’s SSL packet inspection practices and the reasons for them. This education should include information about the privacy implications of SSL packet inspection.
- Regularly Review and Update: The SSL packet inspection configuration and policies should be regularly reviewed and updated to ensure that they are effective and compliant with all applicable laws and regulations.
- Consider Selective Decryption: Implement selective decryption, focusing on specific traffic types or users, to minimize the performance impact and privacy concerns. This approach allows for targeted inspection where it’s most needed.
Alternatives to SSL Packet Inspection
While SSL packet inspection is a valuable security tool, it’s not the only option available. Other approaches to securing encrypted traffic include:
- Endpoint Security: Endpoint security solutions can detect and block threats before they are encrypted and transmitted over the network.
- Network Segmentation: Network segmentation can limit the impact of a security breach by isolating sensitive data and applications.
- Threat Intelligence: Threat intelligence feeds can provide information about known threats and vulnerabilities, which can be used to improve security defenses.
- DNS Filtering: DNS filtering can block access to malicious websites and prevent malware from communicating with command-and-control servers.
The Future of SSL Packet Inspection
As encryption becomes more prevalent and sophisticated, SSL packet inspection will continue to be an important security tool. However, the challenges associated with SSL packet inspection will also continue to grow. Organizations will need to stay up-to-date on the latest technologies and best practices to ensure that they can effectively secure their networks without compromising user privacy or performance.
One key trend is the increasing use of Perfect Forward Secrecy (PFS) and Elliptic-Curve Cryptography (ECC), which make it more difficult to decrypt SSL/TLS traffic. This requires advanced inspection techniques and more powerful hardware. Additionally, the adoption of protocols like TLS 1.3 further complicates the inspection process, requiring security solutions to adapt to these evolving standards.
Another trend is the growing emphasis on privacy. As users become more aware of the privacy implications of SSL packet inspection, organizations will need to be more transparent about their practices and implement stronger privacy controls. This may involve using techniques like data masking or anonymization to protect sensitive information.
Conclusion
SSL packet inspection is a powerful security tool that can help organizations protect themselves from threats hidden within encrypted traffic. However, it’s important to understand the risks and challenges associated with SSL packet inspection and to implement it in a responsible and ethical manner. By following best practices and staying up-to-date on the latest technologies, organizations can effectively secure their networks without compromising user privacy or performance. It is crucial to weigh the benefits against the potential drawbacks and ensure compliance with relevant regulations and ethical considerations when deploying SSL packet inspection.
[See also: Network Security Best Practices]
[See also: Understanding TLS 1.3]
[See also: Data Loss Prevention Strategies]
