The Ultimate Guide to IP Port Proxy Lists: Everything You Need to Know
In today’s interconnected world, online privacy and security are paramount. One of the tools frequently employed to enhance these aspects is the use of proxies. Specifically, IP port proxy lists are invaluable resources for individuals and organizations seeking to mask their IP addresses, bypass geographical restrictions, and improve their overall online experience. This comprehensive guide delves into the intricacies of IP port proxy lists, explaining what they are, how they work, their benefits, potential risks, and best practices for utilizing them effectively.
Understanding IP Addresses and Ports
Before diving into the specifics of IP port proxy lists, it’s crucial to understand the fundamental concepts of IP addresses and ports. An IP (Internet Protocol) address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. Think of it as your device’s postal address on the internet.
A port, on the other hand, is a virtual point where network connections start and end. Ports are identified by numbers, and they allow different applications on the same device to communicate over the network. For example, web traffic typically uses port 80 (HTTP) or 443 (HTTPS).
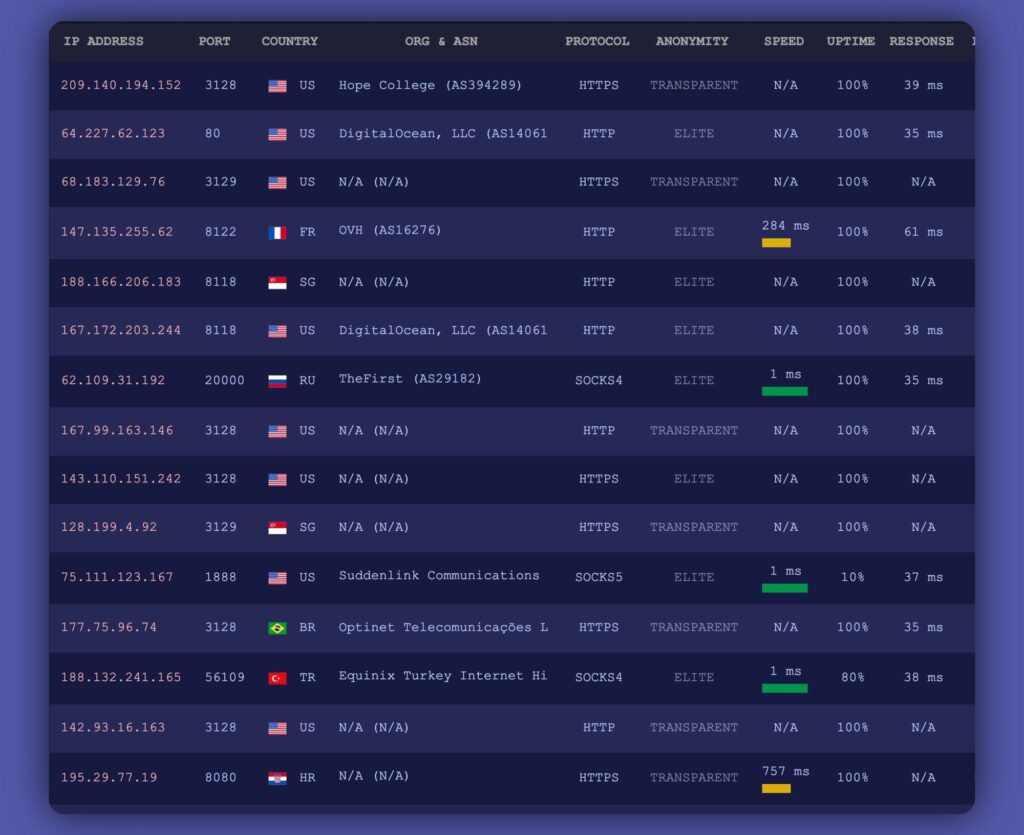
What is an IP Port Proxy List?
An IP port proxy list is a compilation of IP addresses and corresponding port numbers of proxy servers. These proxy servers act as intermediaries between your device and the internet. When you use a proxy, your internet traffic is routed through the proxy server, which then forwards it to the destination server. The destination server sees the proxy server’s IP address instead of your actual IP address, thus masking your identity and location.
Types of Proxies Found in IP Port Proxy Lists
IP port proxy lists can contain different types of proxies, each offering varying levels of anonymity and security:
- HTTP Proxies: These proxies are specifically designed for web traffic (HTTP and HTTPS). They are commonly used for general web browsing and accessing websites.
- SOCKS Proxies: SOCKS (Socket Secure) proxies are more versatile and can handle various types of traffic, including web, email, and FTP. They provide a higher level of anonymity compared to HTTP proxies.
- Transparent Proxies: These proxies do not hide your IP address; instead, they identify themselves as proxies and pass your IP address along to the destination server. They are often used for caching content and monitoring internet usage.
- Anonymous Proxies: These proxies hide your IP address but identify themselves as proxies. They provide a moderate level of anonymity.
- Elite Proxies (Highly Anonymous Proxies): These proxies do not reveal your IP address and do not identify themselves as proxies. They offer the highest level of anonymity.
Benefits of Using IP Port Proxy Lists
Utilizing IP port proxy lists offers several benefits, including:
- Enhanced Privacy: By masking your IP address, proxies help protect your online identity and prevent websites and advertisers from tracking your browsing activity.
- Bypassing Geographical Restrictions: Some websites and services are only available in certain regions. Proxies can be used to bypass these restrictions by routing your traffic through a server located in an allowed region.
- Improved Security: Proxies can add an extra layer of security by shielding your device from direct exposure to the internet. This can help protect against certain types of cyberattacks.
- Accessing Blocked Content: In some situations, organizations or governments may block access to certain websites or online content. Proxies can be used to circumvent these blocks.
- Load Balancing: In enterprise environments, proxies can distribute network traffic across multiple servers, improving performance and reliability.
Finding and Using IP Port Proxy Lists
IP port proxy lists can be found through various online resources, including websites, forums, and specialized proxy list providers. However, it’s important to exercise caution when using these lists, as they may contain proxies that are unreliable, slow, or even malicious. [See also: How to Choose a Reliable Proxy Service]
Steps for Using an IP Port Proxy List
- Find a Reputable List: Search for IP port proxy lists from trusted sources. Look for lists that are regularly updated and monitored for quality.
- Test the Proxies: Before using a proxy, test its speed and reliability using online proxy checker tools. This will help you identify proxies that are working and suitable for your needs.
- Configure Your Browser or Application: Configure your web browser or other applications to use the selected proxy. The exact steps will vary depending on the browser or application you are using.
- Verify the Proxy is Working: After configuring the proxy, verify that it is working correctly by checking your IP address on a website like whatismyip.com. The IP address displayed should be the proxy server’s IP address, not your own.
Risks and Considerations When Using IP Port Proxy Lists
While IP port proxy lists offer several benefits, it’s important to be aware of the potential risks and considerations associated with their use:
- Security Risks: Some proxy servers may be operated by malicious actors who could intercept your traffic and steal your data. It’s crucial to use proxies from trusted sources and avoid entering sensitive information while using a proxy.
- Slow Speeds: Free proxies are often overcrowded and can be very slow, leading to a poor browsing experience.
- Unreliability: Proxies can go offline unexpectedly, disrupting your internet connection.
- Logging: Some proxy servers may log your browsing activity, which could compromise your privacy.
- Legal Issues: Using proxies to bypass geographical restrictions or access blocked content may violate the terms of service of certain websites or services.
Best Practices for Using IP Port Proxy Lists
To mitigate the risks and maximize the benefits of using IP port proxy lists, follow these best practices:
- Use Reputable Sources: Only use IP port proxy lists from trusted and well-known sources.
- Regularly Update Your List: Proxy servers can become unreliable or even malicious over time. Regularly update your list to ensure you are using working and safe proxies.
- Test Proxies Before Use: Always test proxies for speed and reliability before using them.
- Use HTTPS Connections: When using a proxy, always use HTTPS connections to encrypt your traffic and protect your data.
- Avoid Entering Sensitive Information: Avoid entering sensitive information, such as passwords or credit card numbers, while using a proxy.
- Consider Paid Proxy Services: If you require reliable and secure proxies, consider using a paid proxy service. Paid services typically offer faster speeds, better security, and more reliable proxies. [See also: Premium Proxy Services vs. Free Proxy Lists]
- Use a VPN in Conjunction: For maximum security and anonymity, consider using a VPN (Virtual Private Network) in conjunction with a proxy. A VPN encrypts all of your internet traffic, providing an additional layer of protection.
Alternatives to IP Port Proxy Lists
While IP port proxy lists can be useful, there are also alternative methods for enhancing online privacy and security:
- Virtual Private Networks (VPNs): VPNs encrypt all of your internet traffic and route it through a secure server, providing a high level of privacy and security.
- Tor Browser: The Tor Browser is a free and open-source browser that anonymizes your internet traffic by routing it through a network of relays.
- Secure DNS Servers: Using secure DNS servers can help protect your DNS queries from being intercepted or manipulated.
Conclusion
IP port proxy lists are a valuable tool for enhancing online privacy, bypassing geographical restrictions, and improving security. However, it’s important to use them with caution and be aware of the potential risks. By following the best practices outlined in this guide, you can mitigate the risks and maximize the benefits of using IP port proxy lists. Remember to always prioritize your online security and privacy, and consider using alternative methods such as VPNs or the Tor Browser for even greater protection. Understanding the nuances of IP port proxy lists empowers you to make informed decisions about your online activity and safeguard your digital footprint. So, whether you’re looking to access region-locked content, protect your browsing history, or simply enhance your online security, IP port proxy lists can be a useful addition to your digital toolkit. Remember to always stay informed and vigilant to ensure a safe and secure online experience.
