Understanding TLS and HTTPS: Securing Your Web Communications
In today’s digital landscape, ensuring the security and privacy of online communications is paramount. Two key technologies that underpin secure web interactions are Transport Layer Security (TLS) and Hypertext Transfer Protocol Secure (HTTPS). While often used interchangeably, they represent distinct yet interconnected components of a secure web experience. This article delves into the intricacies of TLS and HTTPS, exploring their functionalities, differences, and significance in maintaining a safe online environment.
What is TLS?
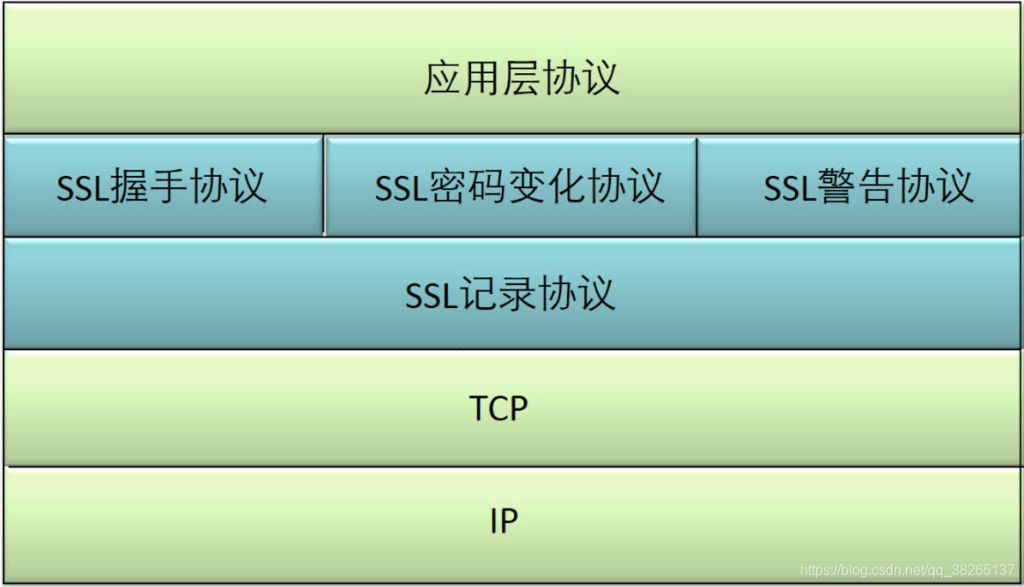
TLS, or Transport Layer Security, is a cryptographic protocol designed to provide secure communication over a network. It’s the successor to Secure Sockets Layer (SSL), although the term SSL is still commonly used. TLS operates at the transport layer of the TCP/IP model, providing encryption and authentication services to applications above it. It ensures that data transmitted between two communicating applications remains confidential, integral, and authenticated.
Key Features of TLS
- Encryption: TLS encrypts data using symmetric-key cryptography after a secure key exchange. This ensures that even if an attacker intercepts the communication, they cannot decipher the data without the correct key.
- Authentication: TLS uses digital certificates to verify the identity of the server (and optionally the client). This prevents man-in-the-middle attacks where an attacker impersonates a legitimate server.
- Integrity: TLS uses message authentication codes (MACs) to ensure that data is not tampered with during transmission. This guarantees that the received data is exactly what was sent.
How TLS Works
The TLS handshake process involves several steps:
- Client Hello: The client sends a “Client Hello” message to the server, specifying the TLS versions, cipher suites, and other parameters it supports.
- Server Hello: The server responds with a “Server Hello” message, selecting the TLS version, cipher suite, and other parameters to use for the connection. The server also sends its digital certificate.
- Certificate Verification: The client verifies the server’s digital certificate against a trusted Certificate Authority (CA). This ensures that the server is who it claims to be.
- Key Exchange: The client and server exchange cryptographic keys using a key exchange algorithm (e.g., RSA, Diffie-Hellman).
- Encryption: Once the key exchange is complete, the client and server use symmetric-key cryptography to encrypt the data transmitted between them.
What is HTTPS?
HTTPS, or Hypertext Transfer Protocol Secure, is the secure version of HTTP, the protocol used for transferring data over the web. HTTPS uses TLS (or SSL) to encrypt communication between a web browser and a web server. This ensures that sensitive data, such as passwords, credit card numbers, and personal information, is protected from eavesdropping and tampering.
The Role of HTTPS in Web Security
HTTPS plays a crucial role in securing web traffic. It provides:
- Confidentiality: By encrypting data, HTTPS prevents unauthorized access to sensitive information.
- Integrity: HTTPS ensures that data is not altered during transmission, protecting against man-in-the-middle attacks.
- Authentication: HTTPS verifies the identity of the server, ensuring that users are connecting to the legitimate website.
HTTPS and Search Engine Optimization (SEO)
In addition to security benefits, HTTPS also has a positive impact on SEO. Search engines like Google prioritize websites that use HTTPS, as it demonstrates a commitment to user security and privacy. Switching to HTTPS can improve a website’s search ranking and visibility. [See also: How to Improve Your Website’s SEO]
TLS vs. HTTPS: Understanding the Difference
While TLS and HTTPS are often used synonymously, it’s important to understand their distinct roles. TLS is a cryptographic protocol that provides secure communication, while HTTPS is a secure version of HTTP that uses TLS (or SSL) to encrypt communication. In essence, HTTPS is HTTP over TLS. TLS is the underlying technology that enables HTTPS to function securely.
Analogy
Think of TLS as the security guard and HTTPS as the building. The security guard (TLS) provides the necessary security measures, such as checking IDs and monitoring access, while the building (HTTPS) is the application that benefits from the security provided by the guard.
Implementing TLS and HTTPS
Implementing TLS and HTTPS involves obtaining a digital certificate from a Certificate Authority (CA) and configuring the web server to use the certificate. Here are the general steps:
- Obtain a Digital Certificate: Choose a Certificate Authority (CA) and purchase a TLS certificate. There are various types of certificates available, such as Domain Validated (DV), Organization Validated (OV), and Extended Validation (EV) certificates. The choice depends on the level of validation required.
- Generate a Certificate Signing Request (CSR): Create a CSR on your web server. The CSR contains information about your organization and domain name.
- Submit the CSR to the CA: Submit the CSR to the CA to request the digital certificate.
- Install the Certificate: Once the CA issues the certificate, install it on your web server.
- Configure the Web Server: Configure your web server to use the TLS certificate and enable HTTPS. This typically involves modifying the server’s configuration file.
- Redirect HTTP to HTTPS: Configure your web server to automatically redirect HTTP traffic to HTTPS. This ensures that all communication is encrypted.
Best Practices for TLS and HTTPS Configuration
To ensure optimal security, it’s important to follow best practices when configuring TLS and HTTPS:
- Use the Latest TLS Version: Always use the latest version of TLS, as it includes the most up-to-date security features and vulnerability patches.
- Choose Strong Cipher Suites: Select strong cipher suites that provide robust encryption and authentication. Avoid weak or outdated cipher suites.
- Enable HTTP Strict Transport Security (HSTS): HSTS instructs web browsers to only access the website over HTTPS, preventing man-in-the-middle attacks.
- Regularly Update Certificates: Ensure that your TLS certificates are regularly updated to maintain security and prevent expiration.
- Monitor for Vulnerabilities: Regularly scan your web server for vulnerabilities and apply security patches promptly.
The Future of TLS and HTTPS
TLS and HTTPS continue to evolve to address emerging security threats and improve performance. New TLS versions are regularly released with enhanced security features and optimizations. The adoption of HTTPS is becoming increasingly widespread, driven by concerns about privacy and security, as well as the positive impact on SEO.
Looking Ahead
The future of TLS and HTTPS will likely see continued advancements in encryption algorithms, authentication methods, and performance optimizations. As web technologies evolve, TLS and HTTPS will remain essential components of a secure and trustworthy online experience. [See also: Future Trends in Cybersecurity]
Conclusion
TLS and HTTPS are fundamental technologies for securing web communications. TLS provides the underlying encryption and authentication mechanisms, while HTTPS leverages TLS to secure HTTP traffic. By understanding the roles of TLS and HTTPS and following best practices for configuration, organizations can ensure the confidentiality, integrity, and authenticity of their online interactions. The continued evolution of these technologies will be crucial in maintaining a safe and secure web environment for users worldwide. Ensuring your website utilizes HTTPS, powered by TLS, is no longer optional but a necessity in today’s digital age, impacting both security and search engine rankings. The implementation of strong TLS configurations and adherence to best practices are vital steps in protecting user data and building trust online. As technology advances, staying informed and adapting to the latest TLS protocols and security measures will be key to maintaining a secure and reliable web presence.
